CISA Domain 3 Training-Information System Acquisition ' 2023
Experts Learn | Cyvitrix
5:46:08
Description
Information System Acquisition and Development - ISACA CISA Training ' 2023
What You'll Learn?
- Become an Information System Auditor or information Security Professional, Achieve your career goals by getting all that you need to know to support your way!
- Learn the fundamentals of IT Audit and Key aspects of Internal and External Auditing
- Understand the Process of Information System Acquisition and IT Project Management metrics!
- Understand Software development, Software testing, changeover and management, and configuration management process.
Who is this for?
What You Need to Know?
More details
DescriptionWelcome to our ALL New CISA Course - Domain 3 +Â Practice Exams
CISA stands for Certified Information Systems Auditor. It is a globally recognized certification in the field of information security auditing, assurance, and control. This certification is awarded by the Information Systems Audit and Control Association (ISACA) to professionals who demonstrate proficiency in auditing, monitoring, controlling, and assessing information systems and technology. CISA certification validates the knowledge and skills required to evaluate and manage information systems and provides a competitive edge to professionals seeking career growth in the field of information security.
If you pursue the Information System Auditing role or Information Security assurance role, this course will be your best guide to gain all the required information and practices that will help you elevate and build your career.
Our CISA Course is up to date, and relevant to CISA CRM version 27 as of July 2023, ISACA announced the new revised version of CISA will be released by 2024, and the updates that the new version may include will be considered in this training as well.
CISA domains are as follows:
1. The Process of Auditing Information Systems
- This domain covers the internal and external audit processes, including audit planning, execution, reporting, and follow-up.
2. Governance and Management of IT
- This domain focuses on the management of IT resources, including policies, procedures, standards, and organizational structure.
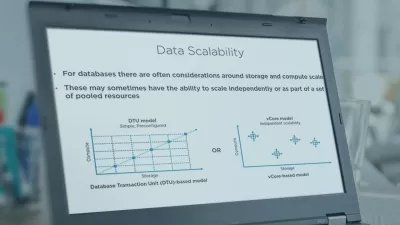
3. Information Systems Acquisition, Development, and Implementation
- This domain covers the process of acquiring, developing, and implementing information systems, including project management, system development life cycle, and change management.
4. Information Systems Operations, Maintenance, and Support
- This domain covers the ongoing operations and maintenance of information systems, including incident management, service management, and asset management.
5. Protection of Information Assets
- This domain covers the protection of information assets, including information security, access controls, encryption, and physical security.
Secure Your Future with Cyvitrix
In today's digital age, cybersecurity and information security are no longer optional. With an increasing amount of sensitive information being stored and shared online, the need for top-notch security has never been greater. Welcome to Cyvitrix, your ultimate resource for comprehensive and cutting-edge cybersecurity courses.
At Cyvitrix, we understand that knowledge is power — power to protect, power to prevent, and power to prosper. Our wide range of courses caters to everyone, from beginners who want to understand the basics to professionals seeking advanced skills to stay ahead of the curve.
Why train with Cyvitrix?
Industry-Relevant Curriculum: We constantly update our courses to reflect the latest threats and trends in cybersecurity. You'll learn how to deal with real-world scenarios, preparing you for the challenges you'll face in the field.
Expert Instructors: Our courses are taught by industry veterans with years of experience in cybersecurity and information security. They're not just teachers, they're practitioners who have been in the trenches.
Flexible Learning: We believe in making learning accessible. Whether you prefer to study at your own pace online or enjoy the intensity of live online classes, we've got you covered.
Certification: Upon completion of our courses, you'll receive a Cyvitrix certification, a testament to your newfound skills and a valuable addition to your professional profile.
Community: Join a network of like-minded learners and experts. Share insights, ask questions, and build connections in our vibrant community.
Whether you're looking to advance your career, start a new one, or simply enhance your understanding of cybersecurity, Cyvitrix is your trusted partner on this journey. With our courses, you're not just investing in education; you're investing in your future.
Take the first step towards empowering your digital life. Enroll in a Cyvitrix course today.
At Cyvitrix, we provide Training courses that help you as students to conquer and pass your certification exams from the first attempt.
Our courses are designed to provide you with all that you need in order not only to pass the exam but also to apply this knowledge to elevate and support your career objectives.
Why training with us is ideal for you?
- Excellent quality video content
- High courses quality
- Organized materials
- Real-life scenarios and examples
- Practice questions and question ideas
- Up-to-date content
- Reasonable pricing
Disclaimer
THIS COURSE CONTAINS NOT ONLY ISACA'S BLUEPRINT FOR THE CISA EXAMINATION BUT ALSO SUPPLEMENTARY VIDEOS AND ARTICLES TO MAKE YOU MASTER THE SUBJECT, THIS COURSE IS VERY LOW-LEVEL.
The objective of this course is to support and supplement the content of ISACA’s official resources. This course is not meant to replace the CISA Review Manual and Question, Answer, and Explanation Manual.
Who this course is for:
- Security analysts, GRC Analysts and Managers
- Students who need to gain understanding in Infosec and cybersecurity
- People who are interested in pursuing this certification
- Accountants and financial analysts
- IT Manager, and Analysts who want to understand and advance their career
- Auditors and Risk practitioners and compliance specialists
- Anyone interested in the subject of the training
Welcome to our ALL New CISA Course - Domain 3 +Â Practice Exams
CISA stands for Certified Information Systems Auditor. It is a globally recognized certification in the field of information security auditing, assurance, and control. This certification is awarded by the Information Systems Audit and Control Association (ISACA) to professionals who demonstrate proficiency in auditing, monitoring, controlling, and assessing information systems and technology. CISA certification validates the knowledge and skills required to evaluate and manage information systems and provides a competitive edge to professionals seeking career growth in the field of information security.
If you pursue the Information System Auditing role or Information Security assurance role, this course will be your best guide to gain all the required information and practices that will help you elevate and build your career.
Our CISA Course is up to date, and relevant to CISA CRM version 27 as of July 2023, ISACA announced the new revised version of CISA will be released by 2024, and the updates that the new version may include will be considered in this training as well.
CISA domains are as follows:
1. The Process of Auditing Information Systems
- This domain covers the internal and external audit processes, including audit planning, execution, reporting, and follow-up.
2. Governance and Management of IT
- This domain focuses on the management of IT resources, including policies, procedures, standards, and organizational structure.
3. Information Systems Acquisition, Development, and Implementation
- This domain covers the process of acquiring, developing, and implementing information systems, including project management, system development life cycle, and change management.
4. Information Systems Operations, Maintenance, and Support
- This domain covers the ongoing operations and maintenance of information systems, including incident management, service management, and asset management.
5. Protection of Information Assets
- This domain covers the protection of information assets, including information security, access controls, encryption, and physical security.
Secure Your Future with Cyvitrix
In today's digital age, cybersecurity and information security are no longer optional. With an increasing amount of sensitive information being stored and shared online, the need for top-notch security has never been greater. Welcome to Cyvitrix, your ultimate resource for comprehensive and cutting-edge cybersecurity courses.
At Cyvitrix, we understand that knowledge is power — power to protect, power to prevent, and power to prosper. Our wide range of courses caters to everyone, from beginners who want to understand the basics to professionals seeking advanced skills to stay ahead of the curve.
Why train with Cyvitrix?
Industry-Relevant Curriculum: We constantly update our courses to reflect the latest threats and trends in cybersecurity. You'll learn how to deal with real-world scenarios, preparing you for the challenges you'll face in the field.
Expert Instructors: Our courses are taught by industry veterans with years of experience in cybersecurity and information security. They're not just teachers, they're practitioners who have been in the trenches.
Flexible Learning: We believe in making learning accessible. Whether you prefer to study at your own pace online or enjoy the intensity of live online classes, we've got you covered.
Certification: Upon completion of our courses, you'll receive a Cyvitrix certification, a testament to your newfound skills and a valuable addition to your professional profile.
Community: Join a network of like-minded learners and experts. Share insights, ask questions, and build connections in our vibrant community.
Whether you're looking to advance your career, start a new one, or simply enhance your understanding of cybersecurity, Cyvitrix is your trusted partner on this journey. With our courses, you're not just investing in education; you're investing in your future.
Take the first step towards empowering your digital life. Enroll in a Cyvitrix course today.
At Cyvitrix, we provide Training courses that help you as students to conquer and pass your certification exams from the first attempt.
Our courses are designed to provide you with all that you need in order not only to pass the exam but also to apply this knowledge to elevate and support your career objectives.
Why training with us is ideal for you?
- Excellent quality video content
- High courses quality
- Organized materials
- Real-life scenarios and examples
- Practice questions and question ideas
- Up-to-date content
- Reasonable pricing
Disclaimer
THIS COURSE CONTAINS NOT ONLY ISACA'S BLUEPRINT FOR THE CISA EXAMINATION BUT ALSO SUPPLEMENTARY VIDEOS AND ARTICLES TO MAKE YOU MASTER THE SUBJECT, THIS COURSE IS VERY LOW-LEVEL.
The objective of this course is to support and supplement the content of ISACA’s official resources. This course is not meant to replace the CISA Review Manual and Question, Answer, and Explanation Manual.
Who this course is for:
- Security analysts, GRC Analysts and Managers
- Students who need to gain understanding in Infosec and cybersecurity
- People who are interested in pursuing this certification
- Accountants and financial analysts
- IT Manager, and Analysts who want to understand and advance their career
- Auditors and Risk practitioners and compliance specialists
- Anyone interested in the subject of the training
User Reviews
Rating
Experts Learn | Cyvitrix
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 41
- duration 5:46:08
- Release Date 2023/10/12