CISA - Certified Information Systems Auditor
Cybersecurity Certificates
7:54:16
Description
This course will help you learn how to audit, control, and secure information system & clear CISA certification
What You'll Learn?
- Info System Auditing: Learn techniques for effective control and governance of information systems.
- IT Governance & Management: Ensure alignment of IT strategy with organizational goals and structures.
- System Acquisition & Development: Master practices for acquiring and developing information systems.
- Protection of Information Assets: Implement controls for information security and privacy.
- Risk Management & Compliance: Grasp frameworks for managing IT risks and ensuring legal compliance
Who is this for?
What You Need to Know?
More details
DescriptionThe Certified Information Systems Auditor (CISA) Training Course is a comprehensive program designed to equip individuals with the knowledge and skills necessary to excel in the field of information systems auditing, control, and security. This course is tailored for professionals who aim to pursue a career as IT auditors or enhance their expertise in assessing and ensuring the security and compliance of IT systems within organizations.
Throughout the course, participants will delve into various topics essential to the practice of IT auditing, including IT governance, risk management, control frameworks, and the auditing process. They will gain a deep understanding of industry best practices and internationally recognized standards, enabling them to identify and mitigate risks, evaluate control effectiveness, and provide valuable insights and recommendations to improve IT systems and processes.
Key Course Highlights:
IT Governance and Management: Participants will explore the principles of IT governance, strategic alignment, and the roles and responsibilities of IT within an organization. They will learn how to align IT goals with business objectives, establish effective IT policies and procedures, and manage IT resources efficiently.
Risk Assessment and Management: The course will cover various aspects of risk assessment and management, including risk identification, analysis, and response strategies. Participants will understand how to evaluate and prioritize risks, develop risk management frameworks, and implement appropriate controls to mitigate identified risks.
Control Frameworks and Standards: Participants will be introduced to widely recognized control frameworks and standards, such as COBIT (Control Objectives for Information and Related Technologies), ISO/IEC 27001, and COSO (Committee of Sponsoring Organizations of the Treadway Commission). They will learn how to assess control frameworks, apply control objectives, and ensure compliance with relevant regulations and standards.
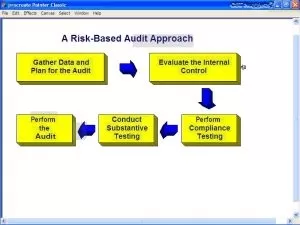
Auditing Processes and Techniques: The course will provide comprehensive insights into the auditing process, including planning, execution, and reporting. Participants will learn auditing techniques, data collection methods, and how to evaluate control effectiveness. They will gain hands-on experience in conducting risk-based audits and performing IT control testing.
Information Systems Operations and Business Resilience: Participants will understand the key aspects of information systems operations, including system development, acquisition, and maintenance. They will also explore business resilience, disaster recovery planning, and incident response strategies to ensure business continuity in the face of disruptions.
Ethics and Professional Conduct: The course emphasizes the importance of professional ethics and conduct in the field of IT auditing. Participants will learn about the ISACA Code of Professional Ethics and other relevant guidelines, focusing on integrity, confidentiality, and professional competence.
By the end of this training course, participants will be well-prepared to undertake the CISA certification exam, as administered by ISACA. They will possess the knowledge and skills necessary to excel in the field of information systems auditing, control, and security, and will be equipped to contribute effectively to the security and compliance of IT systems within organizations.
Who this course is for:
- Information Systems Auditors
- IT Professionals
- Security Professionals
- Compliance Officers and Risk Managers
The Certified Information Systems Auditor (CISA) Training Course is a comprehensive program designed to equip individuals with the knowledge and skills necessary to excel in the field of information systems auditing, control, and security. This course is tailored for professionals who aim to pursue a career as IT auditors or enhance their expertise in assessing and ensuring the security and compliance of IT systems within organizations.
Throughout the course, participants will delve into various topics essential to the practice of IT auditing, including IT governance, risk management, control frameworks, and the auditing process. They will gain a deep understanding of industry best practices and internationally recognized standards, enabling them to identify and mitigate risks, evaluate control effectiveness, and provide valuable insights and recommendations to improve IT systems and processes.
Key Course Highlights:
IT Governance and Management: Participants will explore the principles of IT governance, strategic alignment, and the roles and responsibilities of IT within an organization. They will learn how to align IT goals with business objectives, establish effective IT policies and procedures, and manage IT resources efficiently.
Risk Assessment and Management: The course will cover various aspects of risk assessment and management, including risk identification, analysis, and response strategies. Participants will understand how to evaluate and prioritize risks, develop risk management frameworks, and implement appropriate controls to mitigate identified risks.
Control Frameworks and Standards: Participants will be introduced to widely recognized control frameworks and standards, such as COBIT (Control Objectives for Information and Related Technologies), ISO/IEC 27001, and COSO (Committee of Sponsoring Organizations of the Treadway Commission). They will learn how to assess control frameworks, apply control objectives, and ensure compliance with relevant regulations and standards.
Auditing Processes and Techniques: The course will provide comprehensive insights into the auditing process, including planning, execution, and reporting. Participants will learn auditing techniques, data collection methods, and how to evaluate control effectiveness. They will gain hands-on experience in conducting risk-based audits and performing IT control testing.
Information Systems Operations and Business Resilience: Participants will understand the key aspects of information systems operations, including system development, acquisition, and maintenance. They will also explore business resilience, disaster recovery planning, and incident response strategies to ensure business continuity in the face of disruptions.
Ethics and Professional Conduct: The course emphasizes the importance of professional ethics and conduct in the field of IT auditing. Participants will learn about the ISACA Code of Professional Ethics and other relevant guidelines, focusing on integrity, confidentiality, and professional competence.
By the end of this training course, participants will be well-prepared to undertake the CISA certification exam, as administered by ISACA. They will possess the knowledge and skills necessary to excel in the field of information systems auditing, control, and security, and will be equipped to contribute effectively to the security and compliance of IT systems within organizations.
Who this course is for:
- Information Systems Auditors
- IT Professionals
- Security Professionals
- Compliance Officers and Risk Managers
User Reviews
Rating
Cybersecurity Certificates
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 65
- duration 7:54:16
- Release Date 2023/08/01