Checkpoint Firewall Home-Lab | CCSA and Beyond
Rajneesh Gupta,Jaimin Pathak
3:17:25
Description
Mastering Checkpoint Firewall: Build Your Home-Lab, Earn CCSA, and Dive Beyond
What You'll Learn?
- Gain a comprehensive understanding of Checkpoint Firewall, from its architecture to key features.
- Explore the various blades offered by Checkpoint Firewall and their functionalities.
- Learn how to configure and manage interfaces within Checkpoint Firewall.
- Understand the importance of Secure Internal Communication (SIC) and how to implement it.
- Streamline firewall management through effective utilization of objects.
- Configure and manage Checkpoint IPS (Intrusion Prevention System) policies.
- Set up High Availability (HA) clusters for continuous network protection.
- Explore real-world use cases and scenarios to apply learned concepts in practical situations.
Who is this for?
What You Need to Know?
More details
DescriptionWelcome to the ultimate guide to Checkpoint Firewall, where you'll journey from the fundamentals to advanced applications, all from the comfort of your own home. This comprehensive course is designed to equip you with the skills needed to deploy, configure, and manage Checkpoint Firewalls, from understanding its architecture to implementing high availability solutions. Whether you're aiming to become Checkpoint Certified Security Administrator (CCSA) or looking to enhance your network security expertise, this course provides the knowledge and practical experience you need.
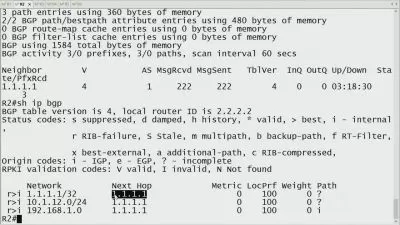
Introduction to Checkpoint Firewall : In this section, you'll delve into the core concepts of Checkpoint Firewall. Learn about its deployment models, architectural components, blade modules, interface configurations, and strategies for ensuring high availability. By understanding these fundamentals, you'll lay a solid foundation for advanced topics in the subsequent sections.
Setting up Home Lab with Gateway and Management Server: Get hands-on experience by setting up your own home-lab environment with Checkpoint Firewall. Walk through the process of deploying a gateway and configuring a management server, enabling you to practice various configurations and scenarios in a safe and controlled environment. Gain practical skills that you can directly apply to real-world scenarios.
Use Cases: Explore real-world use cases and scenarios where Checkpoint Firewall shines. From network segmentation to threat prevention and VPN configurations, you'll discover how Checkpoint Firewall can be leveraged to address diverse security challenges. Gain insights into best practices and strategies for optimizing Checkpoint Firewall deployments based on specific organizational needs.
Whether you're a security professional seeking certification or an IT enthusiast looking to expand your knowledge, this course provides the guidance and resources you need to excel in the world of Checkpoint Firewall. Unlock new opportunities and take your network security skills to the next level with Checkpoint Firewall Home-Lab | CCSA and Beyond.
Who this course is for:
- Network administrators seeking to enhance their skills in firewall management.
- IT professionals aspiring to become Checkpoint Certified Security Administrators (CCSA).
- Cybersecurity analysts interested in bolstering their knowledge of firewall technologies.
- System administrators responsible for network security within their organizations.
- Security engineers aiming to deepen their understanding of Checkpoint Firewall.
- IT consultants looking to expand their expertise in network security solutions.
- Students pursuing degrees or certifications in cybersecurity or network administration.
Welcome to the ultimate guide to Checkpoint Firewall, where you'll journey from the fundamentals to advanced applications, all from the comfort of your own home. This comprehensive course is designed to equip you with the skills needed to deploy, configure, and manage Checkpoint Firewalls, from understanding its architecture to implementing high availability solutions. Whether you're aiming to become Checkpoint Certified Security Administrator (CCSA) or looking to enhance your network security expertise, this course provides the knowledge and practical experience you need.
Introduction to Checkpoint Firewall : In this section, you'll delve into the core concepts of Checkpoint Firewall. Learn about its deployment models, architectural components, blade modules, interface configurations, and strategies for ensuring high availability. By understanding these fundamentals, you'll lay a solid foundation for advanced topics in the subsequent sections.
Setting up Home Lab with Gateway and Management Server: Get hands-on experience by setting up your own home-lab environment with Checkpoint Firewall. Walk through the process of deploying a gateway and configuring a management server, enabling you to practice various configurations and scenarios in a safe and controlled environment. Gain practical skills that you can directly apply to real-world scenarios.
Use Cases: Explore real-world use cases and scenarios where Checkpoint Firewall shines. From network segmentation to threat prevention and VPN configurations, you'll discover how Checkpoint Firewall can be leveraged to address diverse security challenges. Gain insights into best practices and strategies for optimizing Checkpoint Firewall deployments based on specific organizational needs.
Whether you're a security professional seeking certification or an IT enthusiast looking to expand your knowledge, this course provides the guidance and resources you need to excel in the world of Checkpoint Firewall. Unlock new opportunities and take your network security skills to the next level with Checkpoint Firewall Home-Lab | CCSA and Beyond.
Who this course is for:
- Network administrators seeking to enhance their skills in firewall management.
- IT professionals aspiring to become Checkpoint Certified Security Administrators (CCSA).
- Cybersecurity analysts interested in bolstering their knowledge of firewall technologies.
- System administrators responsible for network security within their organizations.
- Security engineers aiming to deepen their understanding of Checkpoint Firewall.
- IT consultants looking to expand their expertise in network security solutions.
- Students pursuing degrees or certifications in cybersecurity or network administration.
User Reviews
Rating
Rajneesh Gupta
Instructor's CoursesJaimin Pathak
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 36
- duration 3:17:25
- Release Date 2024/06/21