Check Point Firewall CCSA R80.40 Training Part2/2
Ahmad Ali
11:01:15
Description
Learn CheckPoint Firewall CCSA R80.40 with Step by Step Lab Workbook
What You'll Learn?
- Configure and Manage CheckPoint Firewall
- How to setup a Lab Environment
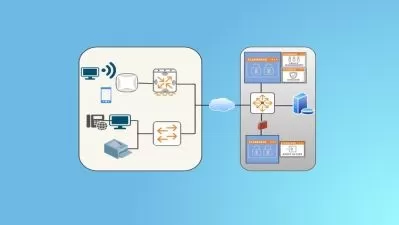
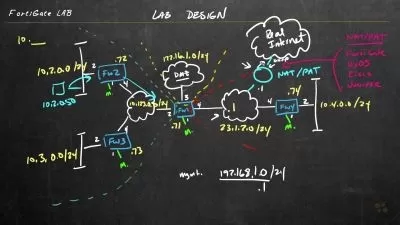
- Understand how to deploy Checkpoint Firewalls in EVE NG
- Configure and Manage CheckPoint User and Group
- Configure and Verify Administrator Accounts
- HTTPS Inspection
- Unified Access Control Policy
- Explicit, Stealth, Cleanup & Mgmt Rules
Who is this for?
More details
DescriptionCheck Point CCSA certification is the very important for IT admins who manage day to day operations of Checkpoint solutions. Here you will get expertise in startup, manage and configure day to day Check Point installations with R80. Course covers how to install R80 security gateway in a distributed environment, configure rules and defines a policy for security, how to work with multiple administrators and how to define permission profiles. After completion of this certification you will be expert in to keep your network secure, you will be expert in evaluating existing security policy, you will be able to manage multiple user access to organization LANs, you will be expert in to monitor any suspicious activities over the internet and you can analyze security attacks better, implement backup for Check Point.
Prerequisites:
You should have basic level knowledge of networking, you should have 6 months to 1-year experience with Check Point products and this is mandatory.
Check Point Primary Products:
Network Security, Software Defined Protection, Public and Private Cloud Security, Zero Trust Remote Access, Data Security, IoT Security, ThreatCloud, ThreatCloud IntelliStore, Virtual Systems, Endpoint Security, Mobile Security, Security Management, Document Security (Capsule Docs product line), Zero-day Protection (SandBlast appliance product line) and Mobile Security (Mobile Threat Prevention product line).
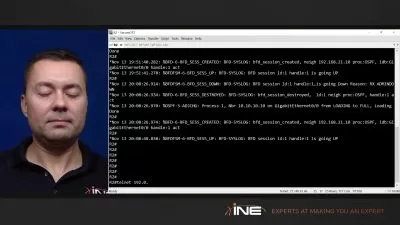
The following course includes lectures on how Check Point features work and the walk-through of the configuration in the lab/production environment. From the very beginning following step-by-step approach you will be able to grasp advanced concepts and step on the next level.
The course is structured in an easy to follow manner starting from the very basic to advanced topics. The topics that are covered are: Installing Check Point in a lab environment, understanding general principles of Firewalling.
THE COURSE INCLUDES:
Introduction to CheckPoint Technology
Building the Lab in EVE-NG
Objects
Admin Accounts
Users and Groups
Site to Site VPN
HA, Load Sharing
Monitoring
Threat
Access Policy
Who this course is for:
- This course is for students trying to obtain the CCSA
- This course is for students trying to learn the Check Point Firewall.
- Any Network or Security Engineer want to learn or polish their Skills.
- System Administrators and Information Security Analysts
- Network Engineers and Security Engineers
Check Point CCSA certification is the very important for IT admins who manage day to day operations of Checkpoint solutions. Here you will get expertise in startup, manage and configure day to day Check Point installations with R80. Course covers how to install R80 security gateway in a distributed environment, configure rules and defines a policy for security, how to work with multiple administrators and how to define permission profiles. After completion of this certification you will be expert in to keep your network secure, you will be expert in evaluating existing security policy, you will be able to manage multiple user access to organization LANs, you will be expert in to monitor any suspicious activities over the internet and you can analyze security attacks better, implement backup for Check Point.
Prerequisites:
You should have basic level knowledge of networking, you should have 6 months to 1-year experience with Check Point products and this is mandatory.
Check Point Primary Products:
Network Security, Software Defined Protection, Public and Private Cloud Security, Zero Trust Remote Access, Data Security, IoT Security, ThreatCloud, ThreatCloud IntelliStore, Virtual Systems, Endpoint Security, Mobile Security, Security Management, Document Security (Capsule Docs product line), Zero-day Protection (SandBlast appliance product line) and Mobile Security (Mobile Threat Prevention product line).
The following course includes lectures on how Check Point features work and the walk-through of the configuration in the lab/production environment. From the very beginning following step-by-step approach you will be able to grasp advanced concepts and step on the next level.
The course is structured in an easy to follow manner starting from the very basic to advanced topics. The topics that are covered are: Installing Check Point in a lab environment, understanding general principles of Firewalling.
THE COURSE INCLUDES:
Introduction to CheckPoint Technology
Building the Lab in EVE-NG
Objects
Admin Accounts
Users and Groups
Site to Site VPN
HA, Load Sharing
Monitoring
Threat
Access Policy
Who this course is for:
- This course is for students trying to obtain the CCSA
- This course is for students trying to learn the Check Point Firewall.
- Any Network or Security Engineer want to learn or polish their Skills.
- System Administrators and Information Security Analysts
- Network Engineers and Security Engineers
User Reviews
Rating
Ahmad Ali
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 62
- duration 11:01:15
- Release Date 2023/05/12