CFE 101 – Cybersecurity for Everyone
David Chapman, PhD
1:07:11
Description
Learn How to Protect Yourself and Your Business from Cyber Threats and Data Breaches
What You'll Learn?
- Identify common threats to information security
- Understand the importance of following security policies and procedures
- Create strong and secure passwords
- Recognize and avoid phishing and social engineering scams
- Secure mobile devices and prevent unauthorized access
- Understand the risks of remote working and public Wi-Fi networks
- Secure physical documents and devices
- Understand the emerging security challenges posed by Generative AI
- Respond to security incidents effectively
Who is this for?
What You Need to Know?
More details
DescriptionCourse Description:
This Cybersecurity Awareness course is designed to equip employees with the knowledge and skills necessary to protect sensitive company data and prevent security breaches. The course covers various aspects of information security, including common threats, best practices for creating and managing passwords, and how to recognize and avoid phishing and social engineering scams. Participants will also learn about physical security, mobile device security, incident response and the implications of generative AI.
What You Will Learn:
Identify common threats to information security
Understand the importance of following security policies and procedures
Create strong and secure passwords
Recognize and avoid phishing and social engineering scams
Secure mobile devices and prevent unauthorized access
Understand the risks of remote working and public Wi-Fi networks
Secure physical documents and devices
Security implications of generative AI
Respond to security incidents effectively
Lectures:
Lecture 1: Cybersecurity for Everyone
- Essence of cybersecurity and its universal relevance
- Case study: Activision's cyberattack and its implications
- Strategies for strong password management, spotting scams, and securing devices & networks
Lecture 2: Making the Most of This Course
- Course structure: video lectures, stories, quizzes
- Emphasis on step-by-step learning
- Importance of self-assessment tools in grasping cybersecurity concepts
Lecture 3: Everyday Information Security Threats
- Overview of prevalent cybersecurity threats
- Case study: Toll Group's struggle with ransomware
- Recognising threats and significance of strong defence mechanisms
Lecture 4: Understanding Malware
- Definition and types of malware
- Malware’s impact on businesses
- Tips to defend against malware
Lecture 5: Why Security Policies & Procedures Matter
- Key components of effective security policies
- Importance of adhering to security guidelines
- Consequences of policy violations for employees and organisations
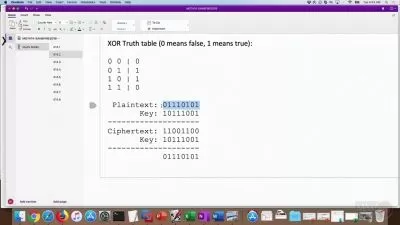
Lecture 6: Password Security
- Creation and importance of strong passwords
- Case study: Deloitte's security incident
- Benefits of two-factor authentication and safe password storage
Lecture 7: Email Security Essentials
- Identifying malicious emails
- How email filtering tools operate
- Top tips to ensure email security
Lecture 8: Guarding Against Social Engineering
- Tactics employed in social engineering
- Seven primary methods used by scammers
- Case studies illustrating risks and prevention
Lecture 9: Staying Ahead of Social Engineering Scams
- Steps to recognise and deter social engineering scams
- Protecting personal information
- Advanced security practices for enhanced safety
Lecture 10: Understanding & Combatting Phishing Attacks
- Definition of phishing attacks
- Different modes of phishing incidents
- Tips and real-life examples to prevent phishing
Lecture 11: Spotting & Dodging Phishing Scams
- How to recognise phishing schemes
- Case study: Toyota Boshoku's phishing incident
- Importance of request verification and continuous updates
Lecture 12: Keeping Your Mobile Safe
- Mobile device security practices
- Case study: UCSF's security oversight
- Measures to protect personal information on mobiles
Lecture 13: Keeping Your Work Safe While Working Remotely
- Best practices for remote work security
- Dangers of public Wi-Fi
- Importance of separating work and personal devices
Lecture 14: Attacks on Remote Workers
- Major cyberattacks targeting remote workers
- Emphasis on adherence to security guidelines
- Importance of vigilant observation and incident reporting
Lecture 15: Staying Safe in the Real World
- Importance of physical security
- Measures to safeguard paper files, gadgets, and workspaces
- How to deter unwanted intruders
Lecture 16: When Safety Fails in the Real World
- Consequences of overlooking physical security
- Case study: Morgan Stanley's security lapse
- Continuous vigilance and secure data handling
Lecture 17: Keep Your Network Safe
- Basics of network security likened to a digital fortress
- Case study: McDonald's security breach
- Tools and practices for network protection
Lecture 18: Generative AI
- Introduction to Generative AI and its business impact
- Case study: Samsung's error and the Zuckerberg 'Deepfake' video
- Maintaining safety in the age of Generative AI
Lecture 19: Incident Response
- Identifying and addressing security incidents
- Case study: NHS's ransomware debacle
- Importance of prompt reporting and bolstering cybersecurity
Lecture 20: Course Recap & Next Steps
- Reiteration of core security concepts
- Importance of holistic cybersecurity
- Ensuring continuous safety in varied contexts.
In this comprehensive course, you'll learn about the various threats to information security and the importance of following security policies and procedures to prevent security breaches. You'll learn how to create strong and secure passwords, recognize and avoid phishing and social engineering scams, and secure mobile devices and prevent unauthorized access.
You'll also understand the risks of remote working and public Wi-Fi networks, as well as the importance of physical security, network security, incident response and the emerging security challenges posed by generative AI.
By the end of this course, you'll have a solid understanding of information security and the knowledge and skills necessary to protect sensitive company data and respond effectively to security incidents. You'll also have the tools and resources necessary to maintain information security and protect your organization from security breaches. Enrol now and start your journey to becoming an information security expert!
Who this course is for:
- Everyone
Course Description:
This Cybersecurity Awareness course is designed to equip employees with the knowledge and skills necessary to protect sensitive company data and prevent security breaches. The course covers various aspects of information security, including common threats, best practices for creating and managing passwords, and how to recognize and avoid phishing and social engineering scams. Participants will also learn about physical security, mobile device security, incident response and the implications of generative AI.
What You Will Learn:
Identify common threats to information security
Understand the importance of following security policies and procedures
Create strong and secure passwords
Recognize and avoid phishing and social engineering scams
Secure mobile devices and prevent unauthorized access
Understand the risks of remote working and public Wi-Fi networks
Secure physical documents and devices
Security implications of generative AI
Respond to security incidents effectively
Lectures:
Lecture 1: Cybersecurity for Everyone
- Essence of cybersecurity and its universal relevance
- Case study: Activision's cyberattack and its implications
- Strategies for strong password management, spotting scams, and securing devices & networks
Lecture 2: Making the Most of This Course
- Course structure: video lectures, stories, quizzes
- Emphasis on step-by-step learning
- Importance of self-assessment tools in grasping cybersecurity concepts
Lecture 3: Everyday Information Security Threats
- Overview of prevalent cybersecurity threats
- Case study: Toll Group's struggle with ransomware
- Recognising threats and significance of strong defence mechanisms
Lecture 4: Understanding Malware
- Definition and types of malware
- Malware’s impact on businesses
- Tips to defend against malware
Lecture 5: Why Security Policies & Procedures Matter
- Key components of effective security policies
- Importance of adhering to security guidelines
- Consequences of policy violations for employees and organisations
Lecture 6: Password Security
- Creation and importance of strong passwords
- Case study: Deloitte's security incident
- Benefits of two-factor authentication and safe password storage
Lecture 7: Email Security Essentials
- Identifying malicious emails
- How email filtering tools operate
- Top tips to ensure email security
Lecture 8: Guarding Against Social Engineering
- Tactics employed in social engineering
- Seven primary methods used by scammers
- Case studies illustrating risks and prevention
Lecture 9: Staying Ahead of Social Engineering Scams
- Steps to recognise and deter social engineering scams
- Protecting personal information
- Advanced security practices for enhanced safety
Lecture 10: Understanding & Combatting Phishing Attacks
- Definition of phishing attacks
- Different modes of phishing incidents
- Tips and real-life examples to prevent phishing
Lecture 11: Spotting & Dodging Phishing Scams
- How to recognise phishing schemes
- Case study: Toyota Boshoku's phishing incident
- Importance of request verification and continuous updates
Lecture 12: Keeping Your Mobile Safe
- Mobile device security practices
- Case study: UCSF's security oversight
- Measures to protect personal information on mobiles
Lecture 13: Keeping Your Work Safe While Working Remotely
- Best practices for remote work security
- Dangers of public Wi-Fi
- Importance of separating work and personal devices
Lecture 14: Attacks on Remote Workers
- Major cyberattacks targeting remote workers
- Emphasis on adherence to security guidelines
- Importance of vigilant observation and incident reporting
Lecture 15: Staying Safe in the Real World
- Importance of physical security
- Measures to safeguard paper files, gadgets, and workspaces
- How to deter unwanted intruders
Lecture 16: When Safety Fails in the Real World
- Consequences of overlooking physical security
- Case study: Morgan Stanley's security lapse
- Continuous vigilance and secure data handling
Lecture 17: Keep Your Network Safe
- Basics of network security likened to a digital fortress
- Case study: McDonald's security breach
- Tools and practices for network protection
Lecture 18: Generative AI
- Introduction to Generative AI and its business impact
- Case study: Samsung's error and the Zuckerberg 'Deepfake' video
- Maintaining safety in the age of Generative AI
Lecture 19: Incident Response
- Identifying and addressing security incidents
- Case study: NHS's ransomware debacle
- Importance of prompt reporting and bolstering cybersecurity
Lecture 20: Course Recap & Next Steps
- Reiteration of core security concepts
- Importance of holistic cybersecurity
- Ensuring continuous safety in varied contexts.
In this comprehensive course, you'll learn about the various threats to information security and the importance of following security policies and procedures to prevent security breaches. You'll learn how to create strong and secure passwords, recognize and avoid phishing and social engineering scams, and secure mobile devices and prevent unauthorized access.
You'll also understand the risks of remote working and public Wi-Fi networks, as well as the importance of physical security, network security, incident response and the emerging security challenges posed by generative AI.
By the end of this course, you'll have a solid understanding of information security and the knowledge and skills necessary to protect sensitive company data and respond effectively to security incidents. You'll also have the tools and resources necessary to maintain information security and protect your organization from security breaches. Enrol now and start your journey to becoming an information security expert!
Who this course is for:
- Everyone
User Reviews
Rating
David Chapman, PhD
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 20
- duration 1:07:11
- Release Date 2023/10/12