Certified CyberCop - Certified Kali Linux Pentester Part - 3
Secbay Inc.
5:08:22
Description
Get free Mock Exam and Flash Cards - Prepared and Developed by Certcop Certified Trainers & Professionals.
What You'll Learn?
- Web Exploiting
- OS Exploiting
- Password Cracking
- Wireless Networking
- Linux Forensics
- Free Flash Cards
Who is this for?
More details
DescriptionCertified Kali Linux Pentester (CKLPT) is NICCS Approved
Secbay's latest Certified Kali Linux PenTester (CKLPT) training & certification program is NICCS approved & it offers On-Demand, Instructor-Led Classroom, and Virtual Live training. This training program is available worldwide.
The student has an option to get certified as a Certified Cybercop - Kali Linux Pentester from Certcop.
About Course
This program is extensively hands-on and will actively engage students in task-focused activities, and lab-based knowledge checks to ensure maximum skill transfer and retention.
This program is designed for IT & Cyber Security professionals who are new to Kali Linux. This program is extensively hands-on and will actively engage students in task-focused activities, and lab-based knowledge checks to ensure maximum skill transfer and retention. In addition, a GUI-based Environment will be featured to build on the student’s existing technical knowledge, while command line concepts will be introduced to provide a foundation for students planning to work full time in the Pen Testing using Kali Linux.
Program Objectives
Installation of Kali Linux
Installation of Virtual Machine
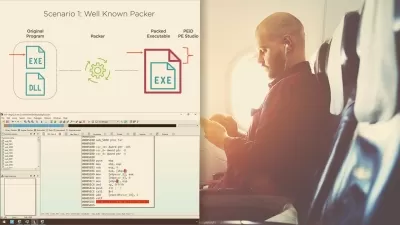
Web Exploitation
OS Exploitation
Password Cracking
Wireless Networking
Linux Forensics
Purpose of the Course:
The materials within this course focus on the Knowledge Skills and Abilities identified within the Specialty Areas like:
Cyber Defense Analysis
Systems Analysis
Technology R&D
Vulnerability Assessment and Management
Basic Linux and Security Concepts
Who this course is for:
- who wish to gain a solid understanding of Kali Linux Pentester and its usage in real world applications.
Certified Kali Linux Pentester (CKLPT) is NICCS Approved
Secbay's latest Certified Kali Linux PenTester (CKLPT) training & certification program is NICCS approved & it offers On-Demand, Instructor-Led Classroom, and Virtual Live training. This training program is available worldwide.
The student has an option to get certified as a Certified Cybercop - Kali Linux Pentester from Certcop.
About Course
This program is extensively hands-on and will actively engage students in task-focused activities, and lab-based knowledge checks to ensure maximum skill transfer and retention.
This program is designed for IT & Cyber Security professionals who are new to Kali Linux. This program is extensively hands-on and will actively engage students in task-focused activities, and lab-based knowledge checks to ensure maximum skill transfer and retention. In addition, a GUI-based Environment will be featured to build on the student’s existing technical knowledge, while command line concepts will be introduced to provide a foundation for students planning to work full time in the Pen Testing using Kali Linux.
Program Objectives
Installation of Kali Linux
Installation of Virtual Machine
Web Exploitation
OS Exploitation
Password Cracking
Wireless Networking
Linux Forensics
Purpose of the Course:
The materials within this course focus on the Knowledge Skills and Abilities identified within the Specialty Areas like:
Cyber Defense Analysis
Systems Analysis
Technology R&D
Vulnerability Assessment and Management
Basic Linux and Security Concepts
Who this course is for:
- who wish to gain a solid understanding of Kali Linux Pentester and its usage in real world applications.
User Reviews
Rating
Secbay Inc.
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 8
- duration 5:08:22
- Release Date 2023/02/28