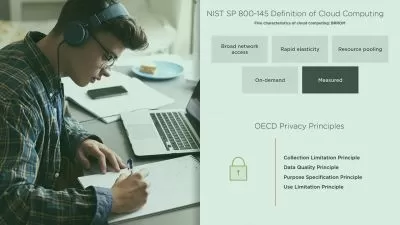
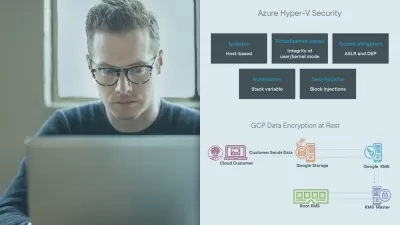
CCSP Cert Prep: 5 Cloud Security Operations
Mike Chapple
2:46:30
Description
The omnipresence of cloud computing in the business world has created a high demand for cybersecurity professionals with cloud expertise. Earning the Certified Cloud Security Professional (CCSP) certification demonstrates that you have the skills needed to help businesses secure information and systems that used to live on site. In this course, learn how security operations function in the world of cloud computing as you prepare for the Certified Cloud Security Professional (CCSP) exam. This course covers the fifth domain of that exam: Cloud Security Operations. Mike Chapple demonstrates how to build, operate, and manage the physical and logical infrastructure required to support cloud computing. Plus, learn about digital forensics and the incident response process.
Note: This course is designed to cover the most recent version of the CCSP exam, released in August 2022.
More details
User Reviews
Rating
Mike Chapple
Instructor's Courses
Linkedin Learning
View courses Linkedin Learning- language english
- Training sessions 50
- duration 2:46:30
- Release Date 2023/01/04



















![Snowflake Mastery: Easy steps to gain expertise [2024]](https://traininghub.ir/image/course_pic/42499-x225.webp)