CCSK v5 Training- Prepare for Cloud Security Certification
Nour | Cyvitrix Train
11:37:22
Description
Master Cloud Security and Prepare for the CCSK Certification
What You'll Learn?
- Cloud computing concepts and architectures, including deployment and service models.
- Cloud governance principles and frameworks, including ISO 27017, CSA STAR, and PCI-DSS.
- Cloud risk management and compliance, including NIST RMF, ISO 31000, and privacy regulations.
- Identity and access management in cloud environments, covering RBAC, SSO, SASE, and CASB.
- Security monitoring, threat detection, and incident response strategies for the cloud.
- Infrastructure and networking in cloud environments, including virtualization, containers, and APIs.
- Cloud workload security, including Docker and Kubernetes security best practices.
- Cloud data security lifecycle, covering encryption, data loss prevention, and key management.
- Application security concepts, including OWASP Top 10, threat modeling, and DevOps security.
- Resilience and incident response, focusing on disaster recovery, business continuity, and SIEM.
- Emerging technologies such as AI, IoT, Blockchain, and their impact on cloud security.
Who is this for?
What You Need to Know?
More details
DescriptionMaster Cloud Security and Prepare for the CCSK Certification
Gain a solid foundation in cloud security with our Certificate of Cloud Security Knowledge (CCSK) course. Created by Ahmed, an experienced cloud security expert, this course is designed to provide you with the essential skills to secure cloud environments and pass the CCSK certification exam confidently.
Why Choose This CCSK Course?
Expert-Led Training: Learn directly from Ahmed, an experienced cloud security professional who has extensive knowledge in cloud computing, security, and governance.
Comprehensive Coverage: Thorough coverage of all domains in the CCSK body of knowledge, ensuring you’re well-prepared for the certification exam.
Real-World Scenarios: Learn through practical examples and case studies, bridging the gap between theoretical concepts and real-world applications.
Exam-Focused Approach: The course content is aligned with the latest CCSK exam blueprint, focusing on the key topics that will help you pass the certification.
Course Highlights
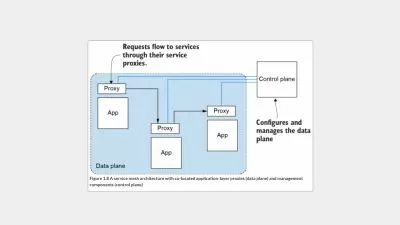
Cloud Computing Concepts and Architecture
Understand the fundamentals of cloud computing, including its models, architectures, and deployment types, and how they affect security.
Governance, Risk Management, and Compliance
Learn how to manage governance, risk, and compliance in cloud environments to ensure cloud adoption aligns with business objectives.
Cloud Security Management
Explore cloud security controls and management practices, including identity and access management, encryption, and data protection.
Infrastructure and Application Security
Understand how to secure cloud infrastructure, applications, and platforms while mitigating risks associated with cloud deployments.
Legal, Contractual, and Operational Challenges
Gain insight into the legal and contractual obligations involved in cloud security, including data sovereignty, privacy, and compliance issues.
DESCLAIMER
This course utilizes advanced text-to-speech technology to deliver the instructor's voice with a clean, crisp, and clear accent, ensuring that learners can easily understand and engage with the content. While most lectures are delivered in a standardized English accent, some may feature non-English native accents. We are actively working to unify the quality across all lectures to provide a consistent experience. If you have any concerns, questions, or feedback, please feel free to reach out to us. Your input is highly valued and helps us improve the course for everyone.
Key Benefits
Complete Coverage of Cloud Security Topics: Detailed training covering all essential aspects of cloud security, providing a comprehensive understanding for the CCSK certification.
Flexible Learning: Access on-demand video lectures, quizzes, and downloadable resources to study at your own pace.
Practice Questions: Regular quizzes and exam-style practice questions to test your knowledge and boost your confidence.
Lifetime Access: Get lifetime access to all course materials and future updates, ensuring you always have the latest information.
Who Should Enroll?
IT and Security Professionals: Those who want to understand cloud security fundamentals and secure cloud environments effectively.
Aspiring CCSK Candidates: Anyone aiming for the CCSK certification and seeking a solid understanding of cloud security.
Cloud Architects and Developers: Professionals involved in designing and developing cloud-based solutions looking to improve their security practices.
Meet Your Instructor
Ahmed is a cloud security expert with years of experience in cloud computing, IT security, and governance. As a certified instructor and cybersecurity consultant across major firms in the Middle East and Europe, Ahmed brings a wealth of real-world knowledge to help you succeed in your cloud security certification journey.
Student Testimonials
"This course was exactly what I needed to prepare for the CCSK exam. Ahmed explains concepts clearly and provides practical examples that make it easy to understand." - Amina R.
"Ahmed's experience and practical approach really shine through. The course is well-structured, and I passed my CCSK exam on the first try!" - John S.
Enroll Now and Start Mastering Cloud Security Knowledge!
Advance your career in cloud security by gaining the essential knowledge required to secure cloud environments and pass the CCSK exam. This course provides everything you need to build a solid foundation in cloud security and succeed as a Certified Cloud Security Knowledge professional.
Enroll Today and start mastering cloud security!
FAQ
What is the CCSK Certification?
The Certificate of Cloud Security Knowledge (CCSK) is a globally recognized certification by the Cloud Security Alliance (CSA) that validates an individual's knowledge of cloud security best practices.
How long will it take to complete the course?
The course is self-paced, allowing you to complete it on your schedule. Most learners finish within a few weeks, depending on their study plan.
Who this course is for:
- IT professionals seeking to expand their cloud security knowledge.
- Cybersecurity specialists looking to secure cloud environments and systems.
- Cloud architects and engineers responsible for implementing secure cloud infrastructures.
- Business leaders aiming to understand cloud security governance and compliance.
- Students or newcomers interested in building a career in cloud security and pursuing the CCSK certification.
Master Cloud Security and Prepare for the CCSK Certification
Gain a solid foundation in cloud security with our Certificate of Cloud Security Knowledge (CCSK) course. Created by Ahmed, an experienced cloud security expert, this course is designed to provide you with the essential skills to secure cloud environments and pass the CCSK certification exam confidently.
Why Choose This CCSK Course?
Expert-Led Training: Learn directly from Ahmed, an experienced cloud security professional who has extensive knowledge in cloud computing, security, and governance.
Comprehensive Coverage: Thorough coverage of all domains in the CCSK body of knowledge, ensuring you’re well-prepared for the certification exam.
Real-World Scenarios: Learn through practical examples and case studies, bridging the gap between theoretical concepts and real-world applications.
Exam-Focused Approach: The course content is aligned with the latest CCSK exam blueprint, focusing on the key topics that will help you pass the certification.
Course Highlights
Cloud Computing Concepts and Architecture
Understand the fundamentals of cloud computing, including its models, architectures, and deployment types, and how they affect security.Governance, Risk Management, and Compliance
Learn how to manage governance, risk, and compliance in cloud environments to ensure cloud adoption aligns with business objectives.Cloud Security Management
Explore cloud security controls and management practices, including identity and access management, encryption, and data protection.Infrastructure and Application Security
Understand how to secure cloud infrastructure, applications, and platforms while mitigating risks associated with cloud deployments.Legal, Contractual, and Operational Challenges
Gain insight into the legal and contractual obligations involved in cloud security, including data sovereignty, privacy, and compliance issues.
DESCLAIMER
This course utilizes advanced text-to-speech technology to deliver the instructor's voice with a clean, crisp, and clear accent, ensuring that learners can easily understand and engage with the content. While most lectures are delivered in a standardized English accent, some may feature non-English native accents. We are actively working to unify the quality across all lectures to provide a consistent experience. If you have any concerns, questions, or feedback, please feel free to reach out to us. Your input is highly valued and helps us improve the course for everyone.
Key Benefits
Complete Coverage of Cloud Security Topics: Detailed training covering all essential aspects of cloud security, providing a comprehensive understanding for the CCSK certification.
Flexible Learning: Access on-demand video lectures, quizzes, and downloadable resources to study at your own pace.
Practice Questions: Regular quizzes and exam-style practice questions to test your knowledge and boost your confidence.
Lifetime Access: Get lifetime access to all course materials and future updates, ensuring you always have the latest information.
Who Should Enroll?
IT and Security Professionals: Those who want to understand cloud security fundamentals and secure cloud environments effectively.
Aspiring CCSK Candidates: Anyone aiming for the CCSK certification and seeking a solid understanding of cloud security.
Cloud Architects and Developers: Professionals involved in designing and developing cloud-based solutions looking to improve their security practices.
Meet Your Instructor
Ahmed is a cloud security expert with years of experience in cloud computing, IT security, and governance. As a certified instructor and cybersecurity consultant across major firms in the Middle East and Europe, Ahmed brings a wealth of real-world knowledge to help you succeed in your cloud security certification journey.
Student Testimonials
"This course was exactly what I needed to prepare for the CCSK exam. Ahmed explains concepts clearly and provides practical examples that make it easy to understand." - Amina R.
"Ahmed's experience and practical approach really shine through. The course is well-structured, and I passed my CCSK exam on the first try!" - John S.
Enroll Now and Start Mastering Cloud Security Knowledge!
Advance your career in cloud security by gaining the essential knowledge required to secure cloud environments and pass the CCSK exam. This course provides everything you need to build a solid foundation in cloud security and succeed as a Certified Cloud Security Knowledge professional.
Enroll Today and start mastering cloud security!
FAQ
What is the CCSK Certification?
The Certificate of Cloud Security Knowledge (CCSK) is a globally recognized certification by the Cloud Security Alliance (CSA) that validates an individual's knowledge of cloud security best practices.
How long will it take to complete the course?
The course is self-paced, allowing you to complete it on your schedule. Most learners finish within a few weeks, depending on their study plan.
Who this course is for:
- IT professionals seeking to expand their cloud security knowledge.
- Cybersecurity specialists looking to secure cloud environments and systems.
- Cloud architects and engineers responsible for implementing secure cloud infrastructures.
- Business leaders aiming to understand cloud security governance and compliance.
- Students or newcomers interested in building a career in cloud security and pursuing the CCSK certification.
User Reviews
Rating
Nour | Cyvitrix Train
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 84
- duration 11:37:22
- Release Date 2025/01/16