CCNP Security Core Online Training
Knox Hutchinson
33:25:09
Description
This intermediate Cisco CCNP Security training covers the objectives in the 350-701 SCOR exam, which is the core exam for the CCNP Security certification.
Cisco's 350-701 SCOR exam tests a broad skill set, including network, cloud, and content security; endpoint protection and detection; secure network access, visibility, and enforcement. Covering these core security technologies will provide you with the knowledge tested by the 350-701 SCOR.
More details
The CCNP Security represents extreme familiarity with core security technologies — that's why this training covers the essentials of implementing and operating core Cisco security technologies.
For anyone who manages their network — or the security of their network, this training is for you. This Cisco training can be also be used for 350-701 SCOR exam prep, onboarding new network engineers, individual or team training plans, or as a Cisco reference resource.
350-701 SCOR: What You Need to Know
For any network administrator using this training for exam preparation, our CCNP Security Core course maps to the Cisco 350-701 SCOR exam objectives, and covers topics such as:
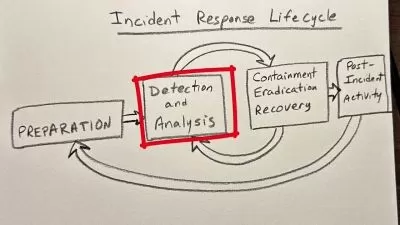
- Understanding information security concepts and strategies, including common attack vectors
- Implementing access controls on Cisco appliances and security technologies
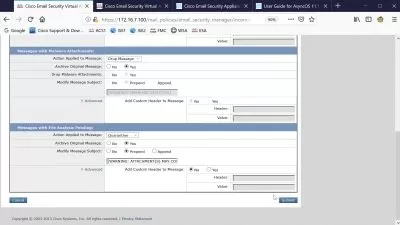
- Implementing email content security features
- Planning for the unique vulnerabilities VPNs can pose to network security
- Locking down networks with Cisco-specific solutions like IOS, VTI VPNs and point-to-point IPsec VPNs
Who Should Take 350-701 SCOR Training?
This CCNP Security Core training is considered Professional-level Cisco training, which means it was designed for network administrators with three to five years of experience with advanced security practices.
New or aspiring network administrators. If you're a new network administrator, getting the training for the CCNP Security Core exam will help ensure that your networks are secure. You don't have to go on to take the exam, or even go for the certification, but instead you can learn the advanced procedures for locking down a network against breaches and hostile actors. There's time for the certification later in your career, in the meantime, why not have a rock-solid and safe network?.
Experienced network administrators. If you've been working as a network administrator for a few years, you may be at a point in your career when you want to focus your expertise and choose a longer-term path. If network security interests you, this CCNP Security Core training can help you make wiser choices within your networks and very wise decisions about a career step toward network security.
User Reviews
Rating
Knox Hutchinson
Instructor's CoursesThe personal touch, coupled with the ability to go at your own pace, makes video training far and away the best way to learn.
Knox brings a wealth of data analysis and visualization experience to CBT Nuggets. Knox started off as a CBT Nuggets learner, became a mentor in our Learner Community, and is now a trainer. Having benefited from the CBT Nuggets Learning Experience firsthand, Knox creates training that connects with learners. Knox also has a wide range of IT experience. Prior to joining CBT Nuggets, Knox worked as an IT consultant, advising in a variety of areas including networking, cloud computing, and project management.
Certifications: Microsoft MCSE: Cloud Platform and Infrastructure, Microsoft MCP: Administering SQL Server 2012/2014 Databases, Cisco DevNet Professional, Cisco CCNP: Enterprise, Certified Meraki Network Operator (CMNO), JNCIA-JUNOS, JNCIA-DevOps, Tableau Desktop Qualified Associate, and CompTIA Network+
Areas of expertise: Data analysis and visualization, business intelligence solutions

CBT Nuggets
View courses CBT Nuggets- language english
- Training sessions 366
- duration 33:25:09
- Release Date 2023/07/21