CCNP and CCIE Security Core SCOR 350-701
Focused View
9:40:31
77 View
001 - Introduction.mp4
02:59
002 - Module introduction.mp4
00:23
003 - Learning objectives.mp4
01:27
004 - 1.1 Understanding Malware, Viruses, Trojans, and Rootkits.mp4
13:33
005 - 1.2 Keyloggers and Spyware.mp4
02:54
006 - 1.3 Malware Analysis Techniques.mp4
03:34
007 - 1.4 Surveying Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attacks.mp4
03:11
008 - 1.5 Surveying Common Application-based Vulnerabilities.mp4
05:27
009 - 1.6 Exploiting Cross-site Scripting (XSS) and Cross-site Request Forgery (CSRF) Vulnerabilities.mp4
07:47
010 - 1.7 Exploiting Authentication and Authorization-based Vulnerabilities.mp4
18:57
011 - 1.8 Understanding SQL Injection and Path Traversal Vulnerabilities.mp4
20:30
012 - 1.9 Understanding Buffer Overflows.mp4
05:33
013 - 1.10 Surveying Unsecure Code Practices and Insecure APIs.mp4
03:57
014 - 1.11 Understanding Security Threats in Cloud Environments.mp4
08:17
015 - 1.12 Understanding IoT Security Threats.mp4
09:32
016 - Learning objectives.mp4
00:39
017 - 2.1 Introducing Cryptography and Cryptanalysis.mp4
01:46
018 - 2.2 Understanding Encryption Protocols.mp4
05:02
019 - 2.3 Describing Hashing Algorithms.mp4
03:54
020 - 2.4 Introducing Public Key Infrastructure (PKI).mp4
05:15
021 - 2.5 Introducing Certificate Authorities (CAs) and Certificate Enrollment.mp4
05:02
022 - 2.6 Surveying SSL and TLS Implementations.mp4
04:21
023 - 2.7 Surveying IPsec Implementations.mp4
14:35
024 - Module introduction.mp4
00:25
025 - Learning objectives.mp4
00:50
026 - 3.1 Introducing SDN.mp4
04:28
027 - 3.2 Explaining North Bound and South Bound APIs in the SDN Architecture.mp4
02:48
028 - 3.3 Introducing Cisco ACI.mp4
06:12
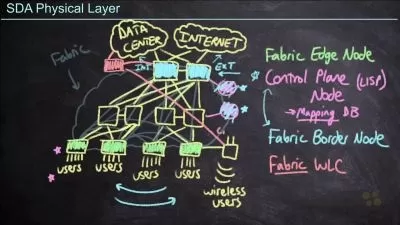
029 - 3.4 Introducing Cisco DNA and Cisco DNA Center.mp4
07:06
030 - 3.5 Understanding VXLAN and Network Overlays.mp4
03:14
031 - 3.6 Understanding Microsegmentation.mp4
04:03
032 - 3.7 Surveying Open Source SDN Solutions.mp4
03:26
033 - 3.8 Understanding the Threats Against SDN Solutions.mp4
02:25
034 - 3.9 Understanding the Security Benefits in SDN Solutions.mp4
01:58
035 - Learning objectives.mp4
01:01
036 - 4.1 Introducing Network Programmability.mp4
08:44
037 - 4.2 Exploring DevNet and DevNet Resources for Security Automation.mp4
01:12
038 - 4.3 Introducing APIs, NETCONF, RESTCONF, and YANG.mp4
11:29
039 - 4.4 A Brief Introduction to Git.mp4
06:10
040 - 4.5 Exploring pxGrid.mp4
05:07
041 - 4.6 Integrating and Automating Security Operations with Cisco Products.mp4
03:27
042 - Module introduction.mp4
00:28
043 - Learning objectives.mp4
00:58
044 - 5.1 Understanding Authentication.mp4
12:28
045 - 5.2 Exploring the RADIUS Protocol.mp4
03:48
046 - 5.3 Surveying the TACACS+ Protocol.mp4
02:35
047 - 5.4 Understanding Authorization.mp4
02:33
048 - 5.5 Surveying Authorization Models.mp4
04:37
049 - 5.6 Defining Accounting.mp4
01:56
050 - 5.7 Exploring Multifactor Authentication and Single Sign-On.mp4
06:26
051 - 5.8 Exploring Examples of Multifactor and Single Sign-On.mp4
01:46
052 - 5.9 Understanding Cisco DUO.mp4
04:39
053 - 5.10 Introducing Cisco ISE.mp4
03:35
054 - 5.11 Understanding Cisco ISE Profiling Services.mp4
03:20
055 - 5.12 Understanding ISE Identity Services.mp4
04:29
056 - 5.13 Describing ISE Authorization Rules.mp4
02:47
057 - Learning objectives.mp4
01:33
058 - 6.1 Defining Network Visibility and Segmentation.mp4
02:20
059 - 6.2 Introducing NetFlow and IPFIX.mp4
02:21
060 - 6.3 Describing Flexible NetFlow Records.mp4
04:19
061 - 6.4 Understanding NetFlow Deployment.mp4
03:10
062 - 6.5 Exploring Cisco Stealthwatch.mp4
01:57
063 - 6.6 Deploying Cisco Stealthwatch Cloud.mp4
03:31
064 - 6.7 On-Premise Monitoring with Stealthwatch Cloud.mp4
00:57
065 - 6.8 Exploring the Cisco TrustSec Solution.mp4
03:34
066 - 6.9 Describing the Benefits of Device Compliance and Application Control.mp4
02:08
067 - 6.10 Introducing Network Segmentation.mp4
01:57
068 - 6.11 Exploring Application-based Segmentation.mp4
02:15
069 - 6.12 Understanding Cisco ACI.mp4
03:12
070 - 6.13 Describing Network Access with CoA.mp4
01:56
071 - 6.14 Integrating Different Security Systems Using pxGrid.mp4
03:29
072 - 6.15 Exploring Cisco Encrypted Traffic Analytics (ETA), Cisco Cognitive Threat Analytics (CTA), and Cisco Threat Grid - CCNP and CCIE Security Core SCOR 350-7.mp4
06:47
073 - Module introduction.mp4
00:31
074 - Learning objectives.mp4
00:57
075 - 7.1 Configuring and Verifying Network Segmentation Using VLANs and VRF-lite.mp4
05:07
076 - 7.2 Configuring and Verifying Port Security.mp4
03:56
077 - 7.3 Configuring and Verifying DHCP Snooping.mp4
03:05
078 - 7.4 Configuring and Verifying Dynamic ARP Inspection.mp4
06:05
079 - 7.5 Exploring and Mitigating Common Layer 2 Threats.mp4
04:30
080 - 7.6 Understanding and Configuring BPDU Guard and Root Guard.mp4
02:21
081 - 7.7 Understanding and Configuring CDP LLDP.mp4
02:55
082 - 7.8 Understanding the Control Plane, Data Plane, and Management Plane.mp4
05:52
083 - 7.9 Exploring How to Secure the Management Plane.mp4
05:20
084 - 7.10 Exploring How to Secure the Control Plane.mp4
06:08
085 - 7.11 Exploring How to Secure the Data Plane.mp4
04:05
086 - Learning objectives.mp4
01:15
087 - 8.1 Introducing Cisco Next-Generation Firewalls.mp4
07:47
088 - 8.2 Surveying the Cisco Firepower Management Center (FMC).mp4
12:49
089 - 8.3 Exploring the Cisco Firepower Device Manager (FDM).mp4
08:35
090 - 8.4 Implementing Access Control Policies.mp4
03:43
091 - Learning objectives.mp4
00:30
092 - 9.1 Introducing Cisco Next-Generation Intrusion Prevention Systems.mp4
05:39
093 - 9.2 Describing Deployment Models of Network Security Solutions and Architectures That Provide Intrusion Prevention Capabilities - CCNP and CCIE Security Core.mp4
01:46
094 - 9.3 Configuring Cisco Next-Generation Intrusion Prevention Systems.mp4
04:35
095 - Module introduction.mp4
00:21
096 - Learning objectives.mp4
00:35
097 - 10.1 Introduction to IPsec Site-to-site and Remote Access VPNs.mp4
08:05
098 - 10.2 Configuring IPsec Site-to-site VPNs.mp4
02:34
099 - 10.3 Configuring Traditional Site-to-site VPN Utilizing Cisco Routers.mp4
03:39
100 - 10.4 Exploring DMVPN.mp4
07:48
101 - 10.5 Understanding GET VPN.mp4
06:00
102 - 10.6 Deploying FlexVPN.mp4
06:59
103 - 10.7 Troubleshooting Site-to-site VPN Implementations.mp4
05:16
104 - Learning objectives.mp4
00:42
105 - 11.1 Introducing Remote Access VPNs.mp4
01:35
106 - 11.2 Exploring Clientless Remote Access VPNs.mp4
04:43
107 - 11.3 Surveying Remote Access VPN Implementations Using Cisco AnyConnect Secure Mobility Client.mp4
02:50
108 - 11.4 Configuring Remote Access VPN in Cisco ASA and in Cisco FTD.mp4
03:41
109 - 11.5 Troubleshooting Remote Access VPN Implementations.mp4
01:36
110 - Module introduction.mp4
00:33
111 - Learning objectives.mp4
00:59
112 - 12.1 Introducing the Different Cloud Deployment and Service Models.mp4
03:49
113 - 12.2 Surveying Patch Management in the Cloud.mp4
03:07
114 - 12.3 Performing Security Assessments in Cloud Environments.mp4
03:15
115 - 12.4 Introducing Agile, DevOps, and CI CD Pipelines.mp4
08:17
116 - 12.5 Introducing Serverless Computing.mp4
01:24
117 - 12.6 Understanding Container Orchestration and an Introduction to Kubernetes.mp4
01:35
118 - 12.7 Exploring the Concepts of DevSecOps.mp4
04:08
119 - 12.8 Surveying Cisco Umbrella.mp4
05:19
120 - 12.9 Exploring Cisco Cloud Email Security.mp4
02:01
121 - 12.10 Exploring Cisco Cloudlock.mp4
04:52
122 - Learning objectives.mp4
01:08
123 - 13.1 Introducing Cisco Content Security Solutions.mp4
03:11
124 - 13.2 Describing Web Proxy Identity and Authentication Including Transparent User Identification.mp4
03:04
125 - 13.3 Introduction to Cisco Email Security.mp4
03:34
126 - 13.4 Exploring the Cisco ESA Deployment Model.mp4
02:21
127 - 13.5 Understanding Email Security Features.mp4
03:54
128 - 13.6 Discussing Email Security in the Cloud.mp4
03:39
129 - 13.7 Introduction to Secure Internet Gateway (SIG).mp4
02:40
130 - 13.8 Describing the Components, Capabilities, and Benefits of Cisco Umbrella.mp4
02:40
131 - 13.9 Exploring Cisco Umbrella Investigate.mp4
03:47
132 - Module introduction.mp4
00:18
133 - Learning objectives.mp4
01:24
134 - 14.1 Introducing AMP for Endpoints.mp4
02:47
135 - 14.2 Describing AMP for Endpoints Outbreak Control.mp4
06:03
136 - 14.3 Comparing Endpoint Threat Detection and Response (ETDR) and Endpoint Detection and Response (EDR) Solutions.mp4
02:51
137 - 14.4 Understanding AMP IP Blacklists and Whitelists.mp4
03:02
138 - 14.5 Exploring Application Control in AMP for Endpoints.mp4
01:22
139 - 14.6 Describing AMP for Endpoints Exclusion Sets.mp4
04:09
140 - 14.7 Introduction to AMP for Endpoints Policies.mp4
00:53
141 - 14.8 Describing the Anyconnect AMP Enabler.mp4
00:35
142 - 14.9 Exploring AMP for Endpoints Engines.mp4
01:29
143 - 14.10 How to Utilize AMP for Endpoints Reporting Features.mp4
03:44
144 - 14.11 Introducing the Cisco Threat Response Solution.mp4
02:31
145 - Summary.mp4
01:40
More details
User Reviews
Rating
average 0
Focused display

LiveLessons
View courses LiveLessonsPearson's video training library is an indispensable learning tool for today's competitive job market. Having essential technology training and certifications can open doors for career advancement and life enrichment. We take learning personally. We've published hundreds of up-to-date videos on wide variety of key topics for Professionals and IT Certification candidates. Now you can learn from renowned industry experts from anywhere in the world, without leaving home.
- language english
- Training sessions 145
- duration 9:40:31
- Release Date 2023/11/07