CCNA Cyber Ops Technology Course SECFND 210-250
Focused View
7:32:06
91 View
1.mp4
03:56
1.mp4
10:44
2.mp4
32:41
3.mp4
28:41
4.mp4
09:19
5.mp4
08:08
6.mp4
10:20
7.mp4
19:47
1.mp4
13:07
2.mp4
06:29
3.mp4
06:22
4.mp4
05:41
1.mp4
07:24
2.mp4
12:40
3.mp4
04:05
4.mp4
05:33
5.mp4
03:46
6.mp4
07:44
7.mp4
11:43
8.mp4
07:29
1.mp4
15:08
2.mp4
11:48
3.mp4
09:06
1.mp4
12:34
2.mp4
09:26
3.mp4
09:24
4.mp4
10:38
5.mp4
07:52
6.mp4
09:09
7.mp4
07:18
1.mp4
14:53
2.mp4
07:47
3.mp4
12:03
1.mp4
06:10
2.mp4
04:10
3.mp4
03:40
4.mp4
05:42
1.mp4
03:37
2.mp4
08:17
3.mp4
05:16
1.mp4
04:42
2.mp4
05:08
1.mp4
08:15
2.mp4
05:16
1.mp4
08:04
2.mp4
06:10
3.mp4
13:31
4.mp4
04:29
1.mp4
06:54
Access Controls.pdf
Antivirus Software.pdf
Asset Management.pdf
Attack Types.pdf
CIA Triad.pdf
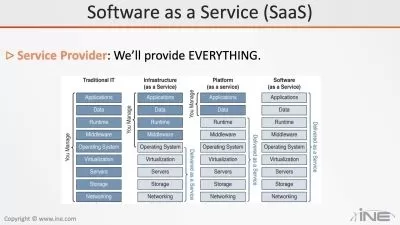
Cloud Options.pdf
Configuration and Change Management.pdf
Course Prerequisites and Overview.pdf
Cryptography.pdf
DNS.pdf
Data Loss Prevention.pdf
Defense-in-Depth.pdf
Digital Forensics.pdf
Ethernet Technology.pdf
Host Firewalls and Sandboxing.pdf
ICMP.pdf
IPv6.pdf
IP Technology.pdf
Identity and Access Management.pdf
Implementing Controls.pdf
Infrastructure Logs.pdf
Least Privilege.pdf
Linux Daemons and Logs.pdf
Linux Permissions and Symlinks.pdf
Linux Processes and Forks.pdf
Log Management.pdf
Mobile Device Management hide01.cyou linuxia.ir.pdf
NetFlow.pdf
Network Models hide01.cyou linuxia.ir.pdf
P2P Applications.pdf
PII and PHI.pdf
Packet Captures.pdf
Password Cracking.pdf
Patch Management.pdf
Public Key Infrastructure.pdf
Reconnaissance and Social Engineering.pdf
Risk Analysis.pdf
SOCs.pdf
Security Evasion.pdf
Security Products.pdf
Security Roles.pdf
TCP and UDP.pdf
Threats.pdf
VPNs and IPsec.pdf
Vulnerability Management.pdf
Windows Event Logs.pdf
Windows Handles and Services.pdf
Windows Processes and Memory.pdf
Windows Registry and WMI.pdf
More details
User Reviews
Rating
average 0
Focused display

INE
View courses INEINE: Expert IT Training for Networking, Cyber Security and Cloud
INE is the trusted global leader in online IT training for networking, cyber security, cloud management, and data science.
- language english
- Training sessions 49
- duration 7:32:06
- Release Date 2023/08/24