Building A Functional Active Directory Environment
Moreblessing Matake
2:07:12
Description
Learn Hands-On How To Built An Functional Active Directory Environment
What You'll Learn?
- Cyber Security
- How Active Directory Environments Are Built
- How to built An Functional Active Directory Environment (Hands-On)
- Learn how to build AD Env From Start To The End
- Managing Active Directory Env
- A skill that 95% of Fortune 100000 companies can put to good use because they implement this service in their networks
- Hands-On I will not waste your time with presentations
Who is this for?
What You Need to Know?
More details
DescriptionCyber Security - Building Active Directory Environments
Dive into the core of Windows networked infrastructure with our comprehensive course, "Mastering Active Directory Deployment and Management." This 250-word guide is expertly crafted to grant IT professionals the expertise needed to build, deploy, and manage Active Directory (AD) environments efficiently.
Throughout this intensive course, you will engage with key aspects of Active Directory, starting with foundational concepts and architecture. You’ll learn how Active Directory serves as the backbone for centralized domain management, facilitating secure user and resource management across a network.
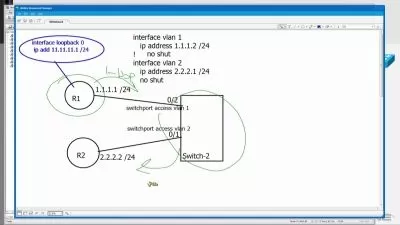
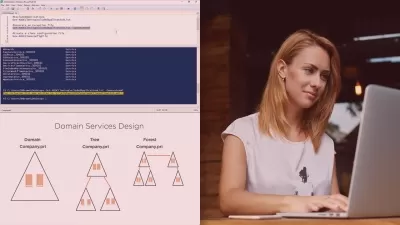
Initial modules focus on the planning phase, covering best practices for designing an AD infrastructure that aligns with organizational needs. You will acquire skills for setting up a domain, adding organizational units, managing domain controllers, and understanding the Global Catalog.
As you progress, hands-on labs will equip you to implement Group Policy Objects (GPOs) for system policy enforcement, automate user and group management, handle secure authentication via Kerberos, and streamline services with Active Directory Federation Services (ADFS).
The course goes beyond basic AD setup, preparing you to deal with complex multi-site deployments, disaster recovery planning, and Active Directory troubleshooting. You'll learn about the integration of cloud services with AD, and how to leverage Azure AD for a hybrid identity management solution.
Whether you're aiming to reinforce your current IT role or to step into a specialized field of network management, this Active Directory course promises a robust skillset to confidently architect, deploy, and oversee active directory environments in the ever-evolving IT landscape. Upon completing this course, you will emerge as a valuable asset in any IT department, ready to handle real-world directory service scenarios effectively.
Join us and future-proof your career with mastery over Active Directory!
Who this course is for:
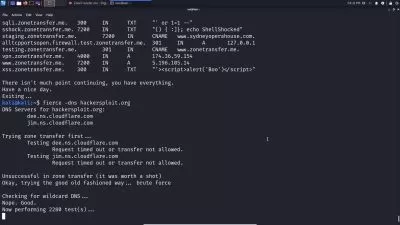
- Ethical Hackers which we call pentesters are going to know & learn how an active directory environments are built & this can help them while they're attacking them cause they will be knowing everything from the ground, For example how it can be built, how can developers make mistakes, what are the most important aspects of an active directory & how they can own an Domain Controller in no time
- Blue Teamers is their responsibility to built them, moniter them, secure them and e.t.c, so it is very important & vital for the defense sides to have this skill in hand
- And of course anyone in the Cyber Security Field who just wanna know how Active Directory Env are built, It is important & Vital to know how to do it cause someday you never know where you might land in this field & please note that 95% of Fortune 1000 companies implement this service in their networks, so just that it is sexy to have this skill in hand
Cyber Security - Building Active Directory Environments
Dive into the core of Windows networked infrastructure with our comprehensive course, "Mastering Active Directory Deployment and Management." This 250-word guide is expertly crafted to grant IT professionals the expertise needed to build, deploy, and manage Active Directory (AD) environments efficiently.
Throughout this intensive course, you will engage with key aspects of Active Directory, starting with foundational concepts and architecture. You’ll learn how Active Directory serves as the backbone for centralized domain management, facilitating secure user and resource management across a network.
Initial modules focus on the planning phase, covering best practices for designing an AD infrastructure that aligns with organizational needs. You will acquire skills for setting up a domain, adding organizational units, managing domain controllers, and understanding the Global Catalog.
As you progress, hands-on labs will equip you to implement Group Policy Objects (GPOs) for system policy enforcement, automate user and group management, handle secure authentication via Kerberos, and streamline services with Active Directory Federation Services (ADFS).
The course goes beyond basic AD setup, preparing you to deal with complex multi-site deployments, disaster recovery planning, and Active Directory troubleshooting. You'll learn about the integration of cloud services with AD, and how to leverage Azure AD for a hybrid identity management solution.
Whether you're aiming to reinforce your current IT role or to step into a specialized field of network management, this Active Directory course promises a robust skillset to confidently architect, deploy, and oversee active directory environments in the ever-evolving IT landscape. Upon completing this course, you will emerge as a valuable asset in any IT department, ready to handle real-world directory service scenarios effectively.
Join us and future-proof your career with mastery over Active Directory!
Who this course is for:
- Ethical Hackers which we call pentesters are going to know & learn how an active directory environments are built & this can help them while they're attacking them cause they will be knowing everything from the ground, For example how it can be built, how can developers make mistakes, what are the most important aspects of an active directory & how they can own an Domain Controller in no time
- Blue Teamers is their responsibility to built them, moniter them, secure them and e.t.c, so it is very important & vital for the defense sides to have this skill in hand
- And of course anyone in the Cyber Security Field who just wanna know how Active Directory Env are built, It is important & Vital to know how to do it cause someday you never know where you might land in this field & please note that 95% of Fortune 1000 companies implement this service in their networks, so just that it is sexy to have this skill in hand
User Reviews
Rating
Moreblessing Matake
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 27
- duration 2:07:12
- Release Date 2024/02/09