Biometrics, Cryptography and AL / ML
ExamIT -Sonia
3:56:50
Description
Biometrics, Cryptography and artificial intelligence/machine learning (AI/ML) for Cybersecurity professionals
What You'll Learn?
- Understand the principles and concepts of biometric authentication and its role in identity verification.
- Learn about encryption, decryption, digital signatures, and key management in cryptography.
- Discover the applications of AI and ML techniques in cybersecurity, including threat detection, anomaly detection, and predictive analytics.
- Understand the ethical and privacy considerations associated with the use of biometrics, cryptography, and AI/ML in cybersecurity.
Who is this for?
What You Need to Know?
More details
DescriptionThis course provides a comprehensive understanding of three critical components in modern cybersecurity: biometrics, cryptography, and artificial intelligence/machine learning (AI/ML). Participants will explore the principles, applications, and practical implementations of these technologies in securing digital systems and protecting sensitive information. Through a combination of theoretical lectures, hands-on exercises, and real-world case studies, learners will develop the knowledge and skills necessary to utilize biometric authentication, cryptographic techniques, and AI/ML algorithms effectively in addressing contemporary cybersecurity challenges.
Course Objectives:
Understand the principles and concepts of biometric authentication and its role in identity verification.
Explore various biometric modalities and their applications in cybersecurity.
Gain insights into cryptographic algorithms, protocols, and methodologies for securing data and communications.
Learn about encryption, decryption, digital signatures, and key management in cryptography.
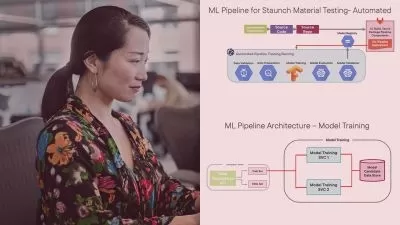
Discover the applications of AI and ML techniques in cybersecurity, including threat detection, anomaly detection, and predictive analytics.
Explore the integration of AI/ML algorithms with security tools and platforms for enhanced protection against cyber threats.
Develop practical skills in implementing biometric authentication systems, cryptographic protocols, and AI-driven security solutions.
Understand the ethical and privacy considerations associated with the use of biometrics, cryptography, and AI/ML in cybersecurity.
By the end of this course, participants will be equipped with the knowledge and skills to leverage biometrics, cryptography, and AI/ML effectively in designing, implementing, and managing cybersecurity solutions tailored to address evolving cyber threats.
Who this course is for:
- Cybersecurity professionals seeking to deepen their knowledge of advanced security technologies.
- IT professionals responsible for implementing and managing security solutions in organizations.
- Security analysts, system administrators, and network engineers interested in leveraging biometrics, cryptography, and AI/ML for cyber defense.
This course provides a comprehensive understanding of three critical components in modern cybersecurity: biometrics, cryptography, and artificial intelligence/machine learning (AI/ML). Participants will explore the principles, applications, and practical implementations of these technologies in securing digital systems and protecting sensitive information. Through a combination of theoretical lectures, hands-on exercises, and real-world case studies, learners will develop the knowledge and skills necessary to utilize biometric authentication, cryptographic techniques, and AI/ML algorithms effectively in addressing contemporary cybersecurity challenges.
Course Objectives:
Understand the principles and concepts of biometric authentication and its role in identity verification.
Explore various biometric modalities and their applications in cybersecurity.
Gain insights into cryptographic algorithms, protocols, and methodologies for securing data and communications.
Learn about encryption, decryption, digital signatures, and key management in cryptography.
Discover the applications of AI and ML techniques in cybersecurity, including threat detection, anomaly detection, and predictive analytics.
Explore the integration of AI/ML algorithms with security tools and platforms for enhanced protection against cyber threats.
Develop practical skills in implementing biometric authentication systems, cryptographic protocols, and AI-driven security solutions.
Understand the ethical and privacy considerations associated with the use of biometrics, cryptography, and AI/ML in cybersecurity.
By the end of this course, participants will be equipped with the knowledge and skills to leverage biometrics, cryptography, and AI/ML effectively in designing, implementing, and managing cybersecurity solutions tailored to address evolving cyber threats.
Who this course is for:
- Cybersecurity professionals seeking to deepen their knowledge of advanced security technologies.
- IT professionals responsible for implementing and managing security solutions in organizations.
- Security analysts, system administrators, and network engineers interested in leveraging biometrics, cryptography, and AI/ML for cyber defense.
User Reviews
Rating
ExamIT -Sonia
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 8
- duration 3:56:50
- Release Date 2024/06/21