Become a Linux Pro: A Comprehensive Guide
Alexander Commodore
3:26:37
Description
Advance Your Career as a Linux Professional with this Comprehensive Guide
What You'll Learn?
- You will learn how to function as a Linux Administrator and Security professional.
- You will be better prepared for Industry Recognized certifications such as CompTIA Linux+, LPI Linux Essentials, and Redhat Certifications.
- You will understand how to configure and secure the Ubuntu 22.04 LTS operating system.
- You will have a strong foundation to pivot to begin ethical hacking learning objectives.
- You will be introduced to basic shell scripting with the BASH language.
- You will gain a unique, comprehensive experience, that is tailored to ease of learning with little fluff.
- You will learn how to create, configure, secure, and connect to Secure Shell servers (SSH).
- You will learn basic Computer and Network security fundamentals that other courses don't teach.
Who is this for?
More details
DescriptionAre you looking to begin a career in Information Technology, Cyber Security, or Systems Administration? If so, learning Linux Administration and Security is an essential step.
Linux is one of the most highly sought-after skills by employers and there is an immediate need for people who have these skills in these career fields. In fact, the majority of all infrastructure running the world runs on Linux/Unix systems.
By gaining exposure and experience with the Linux operating system, from a beginner level to a more advanced level, you'll be giving yourself a competitive advantage in the job market.
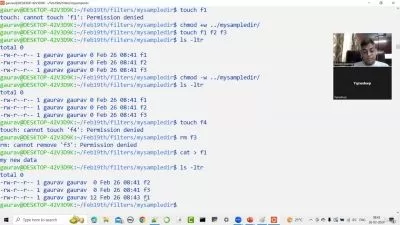
Our Linux administration and security course is designed to help you become an advanced user of Linux that goes beyond just simple command line introductions.
You'll learn from experienced professionals how to use the Linux operating system to its full potential and gain a thorough understanding of computer and network security concepts that are industry standards.
Not only will this course give you valuable hands-on experience with Linux, it will also help you prepare for industry-recognized certifications such as CompTIA Linux+, CySA+, CASP+, PenTest+, LPI Linux Essentials, and RedHat Certifications. There is no better way to complement your academic studies with real-world experience and practice.
By learning Linux, you'll also be setting the foundations for acquiring other skills, such as setting up ideal developer environments or pivoting into learning how to become an ethical hacker. And by gaining experience with this operating system, you'll be able to elevate your professional value and set yourself apart from other candidates who may lack a defined experience with Linux.
Don't miss out on this opportunity to gain valuable skills and experience that can help you succeed in a rewarding career in Information Technology, Cyber Security, or Systems Administration. Sign up for our Linux administration and security course now and take the first step towards a successful career in this exciting and in-demand field.
Who this course is for:
- Anyone who wants to become an advanced user with Linux operating systems.
- Anyone who wants to earn Linux Industry Recognized certifications.
- Anyone who wants to enter IT / Cyber Security.
- Anyone who wants hands on training in a lab environment to add to their experiences.
- Anyone who is looking to add greater professional value to their portfolio.
- Up and coming / Aspiring Junior Linux Systems Administrators
Are you looking to begin a career in Information Technology, Cyber Security, or Systems Administration? If so, learning Linux Administration and Security is an essential step.
Linux is one of the most highly sought-after skills by employers and there is an immediate need for people who have these skills in these career fields. In fact, the majority of all infrastructure running the world runs on Linux/Unix systems.
By gaining exposure and experience with the Linux operating system, from a beginner level to a more advanced level, you'll be giving yourself a competitive advantage in the job market.
Our Linux administration and security course is designed to help you become an advanced user of Linux that goes beyond just simple command line introductions.
You'll learn from experienced professionals how to use the Linux operating system to its full potential and gain a thorough understanding of computer and network security concepts that are industry standards.
Not only will this course give you valuable hands-on experience with Linux, it will also help you prepare for industry-recognized certifications such as CompTIA Linux+, CySA+, CASP+, PenTest+, LPI Linux Essentials, and RedHat Certifications. There is no better way to complement your academic studies with real-world experience and practice.
By learning Linux, you'll also be setting the foundations for acquiring other skills, such as setting up ideal developer environments or pivoting into learning how to become an ethical hacker. And by gaining experience with this operating system, you'll be able to elevate your professional value and set yourself apart from other candidates who may lack a defined experience with Linux.
Don't miss out on this opportunity to gain valuable skills and experience that can help you succeed in a rewarding career in Information Technology, Cyber Security, or Systems Administration. Sign up for our Linux administration and security course now and take the first step towards a successful career in this exciting and in-demand field.
Who this course is for:
- Anyone who wants to become an advanced user with Linux operating systems.
- Anyone who wants to earn Linux Industry Recognized certifications.
- Anyone who wants to enter IT / Cyber Security.
- Anyone who wants hands on training in a lab environment to add to their experiences.
- Anyone who is looking to add greater professional value to their portfolio.
- Up and coming / Aspiring Junior Linux Systems Administrators
User Reviews
Rating
Alexander Commodore
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 64
- duration 3:26:37
- Release Date 2023/01/24