Become a Cybersecurity Expert The Ultimate Blackhat Mastery
Focused View
5:04:16
0 View
1. Introduction To Course.mp4
03:58
2. Labs Prepration.mp4
14:44
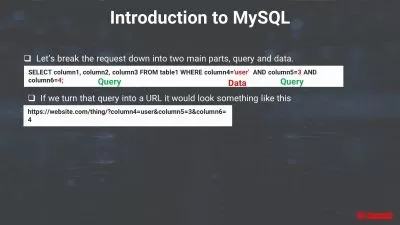
3. Carding.mp4
15:06
4. Malwares Introduction.mp4
08:25
5. Trojans Prectical.mp4
12:52
6. Trojan Icon Changing.mp4
04:52
7. Introduction to VPS.mp4
13:07
8. Hacking From Internet (VPS).mp4
04:49
9. AV Working.mp4
13:46
10. AV Bypassing.mp4
12:38
11. Ransomwares.mp4
12:09
12. Malware Forensics.mp4
08:55
13. Trojans with Science.mp4
16:04
14. Silent Exploits.mp4
12:42
15. Phishing Basics.mp4
06:20
16. Phishing Manually.mp4
09:28
17. Phishing Hosting.mp4
11:33
18. Email Extraction.mp4
07:25
19. Cat Phishing.mp4
11:22
20. Identity Hiding.mp4
10:46
21. Identity Hiding 2.mp4
11:40
22. Identity Hiding 3.mp4
04:19
23. Calling Scams.mp4
11:26
24. Tips and Experience.mp4
11:08
25. Social Engineering.mp4
08:52
26. Social Engineering 2.mp4
08:17
27. Social Engineering 3.mp4
07:42
28. SMTP Introduction.mp4
12:28
29. Cpanel SMTP.mp4
10:20
30. Next Steps in Black Hat.mp4
07:03
More details
User Reviews
Rating
average 0
Focused display
Category

Udemy
View courses UdemyStudents take courses primarily to improve job-related skills.Some courses generate credit toward technical certification. Udemy has made a special effort to attract corporate trainers seeking to create coursework for employees of their company.
- language english
- Training sessions 30
- duration 5:04:16
- Release Date 2024/11/03