AZ-500 Microsoft Azure Security Technologies with SIMS
John Christopher
9:47:29
Description
Get prepared for the AZ-500 exam with instructor led labs and hands on simulations available 24/7
What You'll Learn?
- Learn the concepts and perform hands on activities needed to pass the AZ-500 exam
- Gain a tremendous amount of knowledge involving securing Microsoft Azure Services
- Get loads of hands on experience with securing Microsoft Azure Services
- Utilize hands on simulations that can be access anytime, anywhere!
Who is this for?
What You Need to Know?
More details
DescriptionWe really hope you'll agree, this training is way more than the average course on Udemy!
Have access to the following:
Training from an instructor of over 20 years who has trained thousands of people and also a Microsoft Certified Trainer
Lecture that explains the concepts in an easy to learn method for someone that is just starting out with this material
Instructor led hands on and simulations to practice that can be followed even if you have little to no experience
TOPICS COVEREDÂ INCLUDINGÂ HANDSÂ ONÂ LECTUREÂ ANDÂ PRACTICEÂ TUTORIALS:
Introduction
Welcome to the course
Understanding the Microsoft Environment
Having a Solid Foundation of Active Directory Domains
Having a Solid Foundation of RAS, DMZ, and Virtualization
Having a Solid Foundation of the Microsoft Cloud Services
Order of concepts covered in the course
Questions for John Christopher
Setting up for hands on
IMPORTANT Using Assignments in the course
Creating a free Azure Account
Activating Azure AD P2 license
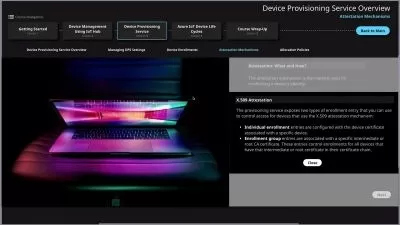
Manage identities in Microsoft Azure Active Directory (Azure AD), part of Microsoft Entra
Visualizing directory services, including Azure AD, Microsoft Entra & Azure ADDS
Create and manage a managed identity for Azure resources
Manage Azure AD users and external identities
Manage Azure AD groups
Manage administrative units
Manage secure access by using Microsoft Azure Active Directory (Azure AD), part of Microsoft Entra
Configure Azure AD Privileged Identity Management (PIM)
Activating a PIM role as a user
Implement Conditional Access policies, including multifactor authentication
Implement Azure AD Identity Protection
Implement passwordless authentication
Configure access reviews
Manage Azure using command line tools
Foundational concepts of using PowerShell
Connecting PowerShell to Azure
Working with Azure AD using PowerShell
Working with Azure Cloudshell
Working with Azure CLI / Bash
Installing Azure CLI on a local machine
Manage application access
Integrate single sign on (SSO) and identity providers for authentication
Create an app registration
Configure app registration permission scopes
Manage app registration permission consent
Manage API permissions to Azure subscriptions and resources
Configure an authentication method for a service principal
Manage access control
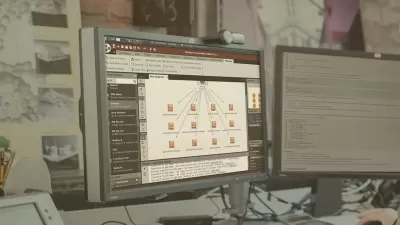
Visualizing Azure role permissions for management groups, subscriptions, resource groups, and resources
Interpret role and resource permissions
Assign built-in roles in Microsoft Azure Active Directory (Azure AD), part of Microsoft Entra
Create and assign custom roles, including Azure roles and Azure AD roles
Implement advanced network security
Secure the connectivity of hybrid networks
Create and configure virtual networks and subnets
Secure the connectivity of virtual networks
Direct traffic through the Azure Firewall
Create and configure Azure Firewall
Create and configure Azure Firewall Manager
Understanding Azure Application Gateway vs Azure Front Door
Create and configure Azure Application Gateway
Create and configure Azure Front Door and Web Application Firewall (WAF)
Configure a resource firewall on a storage account
Visualizing Azure Service Endpoints and Private Endpoints
Implement Azure Service Endpoints and Private Endpoints
Implement Azure DDoS Protection
Deleting resources from previous lessons
Configure advanced security for compute
Configure Endpoint Protection for virtual machines (VMs)
Implement and manage security updates for VMs
Configure security for container services
Manage access to Azure Container Registry
Configure security for serverless compute
Configure security for an Azure App Service
Configure encryption at rest
Configure encryption in transit
Configure centralized policy management
Configure a custom security policy
Create a policy initiative
Configure security settings and auditing by using Azure Policy
Configure and manage threat protection
Concepts of Microsoft Defender for Cloud
Configure Microsoft Defender for Servers (not including Microsoft Defender for Endpoint)
Evaluate for vulnerabilities using Microsoft Defender for Cloud
Configure Microsoft Defender for SQL
Configure and manage security monitoring solutions
Create and customize alert rules by using Azure Monitor
Configure diagnostic logging and log retention by using Azure Monitor
Monitor security logs by using Azure Monitor
Understanding Microsoft Sentinel
Create a log analytics workspace needed for Microsoft Sentinel
Implement Microsoft Sentinel
Configure security for storage
Creating a storage account
Configure access control for storage accounts
Configure storage account access keys
Configure Azure Files identity-based authentication for SMB access
Configure delegated access
Configure security for data
Enable a SQL Database/Server and connect with SSMS
Configure SQL firewall settings for client connections
Enable database authentication by using Microsoft Azure AD, part of Microsoft Entra
Enable database auditing
Configure dynamic masking on SQL workloads
Implement database encryption for Azure SQL Database
Implement network isolation for data solutions, including Synapse Analytics & Cosmos DB
Configure and manage Azure Key Vault
Create and configure Key Vault
Configure access to Key Vault
Manage certificates, secrets, and keys
Configure key rotation
Configure backup and recovery of certificates, secrets, and keys
Finishing Up
Where do I go from here?
Who this course is for:
- IT people interested in learning and passing the Microsoft AZ-500 exam!
- IT people interested in learning a tremendous amount about security in Microsoft Azure Services!
We really hope you'll agree, this training is way more than the average course on Udemy!
Have access to the following:
Training from an instructor of over 20 years who has trained thousands of people and also a Microsoft Certified Trainer
Lecture that explains the concepts in an easy to learn method for someone that is just starting out with this material
Instructor led hands on and simulations to practice that can be followed even if you have little to no experience
TOPICS COVEREDÂ INCLUDINGÂ HANDSÂ ONÂ LECTUREÂ ANDÂ PRACTICEÂ TUTORIALS:
Introduction
Welcome to the course
Understanding the Microsoft Environment
Having a Solid Foundation of Active Directory Domains
Having a Solid Foundation of RAS, DMZ, and Virtualization
Having a Solid Foundation of the Microsoft Cloud Services
Order of concepts covered in the course
Questions for John Christopher
Setting up for hands on
IMPORTANT Using Assignments in the course
Creating a free Azure Account
Activating Azure AD P2 license
Manage identities in Microsoft Azure Active Directory (Azure AD), part of Microsoft Entra
Visualizing directory services, including Azure AD, Microsoft Entra & Azure ADDS
Create and manage a managed identity for Azure resources
Manage Azure AD users and external identities
Manage Azure AD groups
Manage administrative units
Manage secure access by using Microsoft Azure Active Directory (Azure AD), part of Microsoft Entra
Configure Azure AD Privileged Identity Management (PIM)
Activating a PIM role as a user
Implement Conditional Access policies, including multifactor authentication
Implement Azure AD Identity Protection
Implement passwordless authentication
Configure access reviews
Manage Azure using command line tools
Foundational concepts of using PowerShell
Connecting PowerShell to Azure
Working with Azure AD using PowerShell
Working with Azure Cloudshell
Working with Azure CLI / Bash
Installing Azure CLI on a local machine
Manage application access
Integrate single sign on (SSO) and identity providers for authentication
Create an app registration
Configure app registration permission scopes
Manage app registration permission consent
Manage API permissions to Azure subscriptions and resources
Configure an authentication method for a service principal
Manage access control
Visualizing Azure role permissions for management groups, subscriptions, resource groups, and resources
Interpret role and resource permissions
Assign built-in roles in Microsoft Azure Active Directory (Azure AD), part of Microsoft Entra
Create and assign custom roles, including Azure roles and Azure AD roles
Implement advanced network security
Secure the connectivity of hybrid networks
Create and configure virtual networks and subnets
Secure the connectivity of virtual networks
Direct traffic through the Azure Firewall
Create and configure Azure Firewall
Create and configure Azure Firewall Manager
Understanding Azure Application Gateway vs Azure Front Door
Create and configure Azure Application Gateway
Create and configure Azure Front Door and Web Application Firewall (WAF)
Configure a resource firewall on a storage account
Visualizing Azure Service Endpoints and Private Endpoints
Implement Azure Service Endpoints and Private Endpoints
Implement Azure DDoS Protection
Deleting resources from previous lessons
Configure advanced security for compute
Configure Endpoint Protection for virtual machines (VMs)
Implement and manage security updates for VMs
Configure security for container services
Manage access to Azure Container Registry
Configure security for serverless compute
Configure security for an Azure App Service
Configure encryption at rest
Configure encryption in transit
Configure centralized policy management
Configure a custom security policy
Create a policy initiative
Configure security settings and auditing by using Azure Policy
Configure and manage threat protection
Concepts of Microsoft Defender for Cloud
Configure Microsoft Defender for Servers (not including Microsoft Defender for Endpoint)
Evaluate for vulnerabilities using Microsoft Defender for Cloud
Configure Microsoft Defender for SQL
Configure and manage security monitoring solutions
Create and customize alert rules by using Azure Monitor
Configure diagnostic logging and log retention by using Azure Monitor
Monitor security logs by using Azure Monitor
Understanding Microsoft Sentinel
Create a log analytics workspace needed for Microsoft Sentinel
Implement Microsoft Sentinel
Configure security for storage
Creating a storage account
Configure access control for storage accounts
Configure storage account access keys
Configure Azure Files identity-based authentication for SMB access
Configure delegated access
Configure security for data
Enable a SQL Database/Server and connect with SSMS
Configure SQL firewall settings for client connections
Enable database authentication by using Microsoft Azure AD, part of Microsoft Entra
Enable database auditing
Configure dynamic masking on SQL workloads
Implement database encryption for Azure SQL Database
Implement network isolation for data solutions, including Synapse Analytics & Cosmos DB
Configure and manage Azure Key Vault
Create and configure Key Vault
Configure access to Key Vault
Manage certificates, secrets, and keys
Configure key rotation
Configure backup and recovery of certificates, secrets, and keys
Finishing Up
Where do I go from here?
Who this course is for:
- IT people interested in learning and passing the Microsoft AZ-500 exam!
- IT people interested in learning a tremendous amount about security in Microsoft Azure Services!
User Reviews
Rating
John Christopher
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 89
- duration 9:47:29
- English subtitles has
- Release Date 2023/09/11