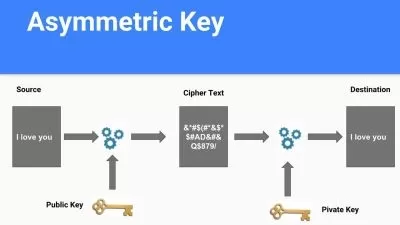
Automated Cyber Security Incident Response: Outfox adversary
Dharmanandana Reddy Pothula
3:17:24
Description
What to Do When Organizations under Cyber Attack and Data Breach
What You'll Learn?
- Cyber Security Architecture with Security operations center & Incident Response
- Prepare organization to handle cyber attacks
- Detection and analysis of cyber attacks
- Handle and respond various cybersecurity incidents systematically
- How to ensure that an organization identify, contain, and recover from cyber attack and mitigate the negative impact on the business operations
- Industry incident response frameworks
- NIST & SANS framework based incident response
- standardized incident response strategy
- Incident response process & policies
- Incident response playbook
- Key Forensic analysis
- Incident Response operation
- Incident Response sandbox
- how to respond after data breach and minimize the loss
- Incident Response process for data breach
- Automated incident response for boosting incident responder analyst's productivity, faster incident detection and response times
- Key tools for the Response & Recovery
- Automated incident response for phishing attacks, bruteforce attacks and zero day vulnerability attacks
- Best Cyber Security Techniques To Prevent Data Breach
- Interview questions on Incident Response
Who is this for?
More details
DescriptionWelcome to the "Automated Cyber Security Incident Response: Outfox adversary"
In this course, we will provide you comprehensive understanding of the cyber security architecture with incident response, NIST cyber security framework with intelligent detection and automated response for the cyber security incident detection and response and the skills needed for the effective and successful data breach investigation
We will start by introducing you to the defense in depth security model based cyber security architecture, NIST cyber security framework with intelligent detection and automated response, and different industry incident frameworks, and prepare you with a solid foundation and methodological approach to handle data breaches and security threats.
As we move deeper, we'll dive into Incident Response Strategy, Incident Response Team, Incident Response Policy & Plan, Incident Playbook, and Incident Response Life Cycle. Subsequently, you will proceed to learning different Incident response phases, Incident detection and analysis of cyber attacks, Investigation methods, deeper forensic analysis, contain and recover from the cyber attacks. After obtaining an understanding of methodological and systematic cyber attacks incident investigation and response, you will advance to learning Incident response operation and sandbox, Automatic incident analysis platform for faster incident detection and response times, and Automated incident response for different scenarios such as phishing attacks, brute force attacks, zero day vulnerability attacks and defend your organization from sophisticated attacks.
This course helps you hone the skills in Defensive techniques, security investigations, and incident handling as incident responder analysts and incident handlers.
Throughout this course, we will use different systematic, methodological approaches and techniques to help you understand the faster and effective Incident response to handle cyber attacks and data breaches.
By the end of this course, you’ll have deeper understanding about the core concepts and how to prepare you to respond efficiently and effectively to cyberthreats.
This course covers concepts of Incident Responder analyst, Incident handler, Blue Team Incident response, CSIRTs, Defensive techniques, security investigations, and incident handling.
You'll also get:
Lifetime Access to The Course
Quick and Friendly Support in the Q&A section
Udemy Certificate of Completion
Do you wish to enhance your skills and boost your employability?
Enroll now to become Professional Incident Handler, Incident Responder Analyst!
See you in the "Automated Cyber Security Incident Response: Outfox adversary" course!
With this course you'll surely get 24/7 support. Please feel free to post your questions in the Q&A section and we'll definitely respond to you within 12 hours.
Who this course is for:
- This course is for those seeking to take major leap into cyber security Incident response
- Anyone interested in learning how to detect and analyse cyber attacks
- Anyone interested in learning how to handle and respond to cybersecurity incidents systematically
- Anyone interested in learning the identification of incidents, response & recovery from cyber attacks
- Anyone interested in learning different industry incident response frameworks
- Anyone interested in learning NIST & SANS framework based incident response
- Anyone interested in learning how to respond after data breach
- Anyone interested in learning automated incident response, SOAR
- Anyone interested in learning Incident response strategy and Process
- Computer security incident response teams (CSIRTs)
- Chief information security officers (CISOs), Chief information officers (CIOs)
- system and network administrators, security staff, technical support staff, computer security program managers, who are responsible for preparing , or responding to security incidents.
- Anyone interested to become Incident handlers and Incident responder analysts
- Anyone one interested to become Blue team Incident response consultant
- Anyone interested in focusing on defensive practices, security investigations, and incident handling
Welcome to the "Automated Cyber Security Incident Response: Outfox adversary"
In this course, we will provide you comprehensive understanding of the cyber security architecture with incident response, NIST cyber security framework with intelligent detection and automated response for the cyber security incident detection and response and the skills needed for the effective and successful data breach investigation
We will start by introducing you to the defense in depth security model based cyber security architecture, NIST cyber security framework with intelligent detection and automated response, and different industry incident frameworks, and prepare you with a solid foundation and methodological approach to handle data breaches and security threats.
As we move deeper, we'll dive into Incident Response Strategy, Incident Response Team, Incident Response Policy & Plan, Incident Playbook, and Incident Response Life Cycle. Subsequently, you will proceed to learning different Incident response phases, Incident detection and analysis of cyber attacks, Investigation methods, deeper forensic analysis, contain and recover from the cyber attacks. After obtaining an understanding of methodological and systematic cyber attacks incident investigation and response, you will advance to learning Incident response operation and sandbox, Automatic incident analysis platform for faster incident detection and response times, and Automated incident response for different scenarios such as phishing attacks, brute force attacks, zero day vulnerability attacks and defend your organization from sophisticated attacks.
This course helps you hone the skills in Defensive techniques, security investigations, and incident handling as incident responder analysts and incident handlers.
Throughout this course, we will use different systematic, methodological approaches and techniques to help you understand the faster and effective Incident response to handle cyber attacks and data breaches.
By the end of this course, you’ll have deeper understanding about the core concepts and how to prepare you to respond efficiently and effectively to cyberthreats.
This course covers concepts of Incident Responder analyst, Incident handler, Blue Team Incident response, CSIRTs, Defensive techniques, security investigations, and incident handling.
You'll also get:
Lifetime Access to The Course
Quick and Friendly Support in the Q&A section
Udemy Certificate of Completion
Do you wish to enhance your skills and boost your employability?
Enroll now to become Professional Incident Handler, Incident Responder Analyst!
See you in the "Automated Cyber Security Incident Response: Outfox adversary" course!
With this course you'll surely get 24/7 support. Please feel free to post your questions in the Q&A section and we'll definitely respond to you within 12 hours.
Who this course is for:
- This course is for those seeking to take major leap into cyber security Incident response
- Anyone interested in learning how to detect and analyse cyber attacks
- Anyone interested in learning how to handle and respond to cybersecurity incidents systematically
- Anyone interested in learning the identification of incidents, response & recovery from cyber attacks
- Anyone interested in learning different industry incident response frameworks
- Anyone interested in learning NIST & SANS framework based incident response
- Anyone interested in learning how to respond after data breach
- Anyone interested in learning automated incident response, SOAR
- Anyone interested in learning Incident response strategy and Process
- Computer security incident response teams (CSIRTs)
- Chief information security officers (CISOs), Chief information officers (CIOs)
- system and network administrators, security staff, technical support staff, computer security program managers, who are responsible for preparing , or responding to security incidents.
- Anyone interested to become Incident handlers and Incident responder analysts
- Anyone one interested to become Blue team Incident response consultant
- Anyone interested in focusing on defensive practices, security investigations, and incident handling
User Reviews
Rating
Dharmanandana Reddy Pothula
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 32
- duration 3:17:24
- Release Date 2023/03/29