Assessing Red Team Post Exploitation Activity
Dale Meredith
1:03:04
Description
In this course, you will explore the mindset and techniques used by red team operators and common cyber adversaries, and the ways the defensive teams can detect and even get ahead of these malicious actions.
What You'll Learn?
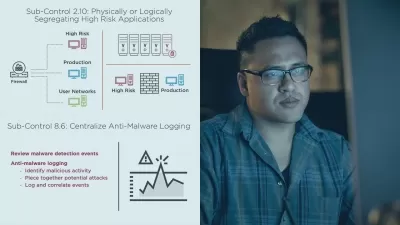
Attackers can use some sophisticated and unsophisticated means to slip by external defenses and detections. Insider threat is on the rise and completely bypasses network or remote access inspection and authentication. As a pen-test progresses from the initial access phase into post-exploitation activity, you aim to understand what is being accomplished inside the network and how your internal defenses can accomplish a defense in depth posture. You ask the assessment team to explain not only what steps they are taking to operate inside your already compromised network but also how you can mitigate these capabilities in the future.
More details
User Reviews
Rating
Dale Meredith
Instructor's Courses
Pluralsight
View courses Pluralsight- language english
- Training sessions 17
- duration 1:03:04
- level average
- Release Date 2023/12/05