Antivirus Evasion - Process Injection and Migration
Moreblessing Matake
1:34:02
Description
Learn Hands-On In Cyber-Security How Red Teamers and Threat Actors (APT) Evade Security Mechanisms in the Real World
What You'll Learn?
- Ethical Hacking
- Installing Kali Linux & Windows Virtual Machines
- Crafting Undetectable Payloads that Bypasses A fully UpTo date Windows Defender Antivirus using Metasploit Shellcode, C# Codes and C++ e.t.c
- Cyber Security
- Process Injection & Migration
- Antivirus Solution Evasion
Who is this for?
What You Need to Know?
More details
DescriptionThis course provides a comprehensive study of process injection and process migration techniques, essential for understanding advanced malware behavior and penetration testing. Participants will explore how attackers use these techniques to execute malicious code, bypass security measures, and evade detection.
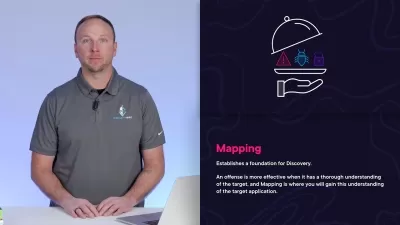
The course covers a range of key techniques, including Classic Process Injection, Process Hollowing, Unhooking AV Hooks, and Unhooking AV ntdll.dll using PerunsFart. These methods allow attackers to stealthily manipulate and hijack legitimate processes. Students will also learn advanced concepts such as Section Mapping, where memory regions are manipulated for stealthy code execution, and Thread Context manipulation to hijack thread execution.
Additionally, participants will explore Asynchronous Procedure Calls (APCs), which allow attackers to queue code execution within a target process, adding to their toolkit of stealth techniques. Emphasis will be placed on understanding how these techniques are used in real-world attacks and how defenders can detect and mitigate them.
Through hands-on labs and case studies, students will gain practical experience in both the offensive use of these techniques and defensive measures, such as behavioral monitoring and memory analysis. The course will also explore detection strategies using modern tools and methodologies like advanced endpoint detection and response (EDR) systems.
By the end, participants will have a deep understanding of process injection and migration, equipping them to defend against these sophisticated attack methods.
Prerequisites: Basic knowledge of operating systems, programming, and cybersecurity fundamentals.
Who this course is for:
- Red Teamers - Leveling their skills in their world of compromising systems & evading security mechanism
- Blue Teamer - Learn how threat actors work or move in the wild, so they can defend better, protect their systems and educate their fellow workers for better security
- Any-One - Off course, anyone in the Cyber Security field who just wanna learn or know how threat actors act in the wild
This course provides a comprehensive study of process injection and process migration techniques, essential for understanding advanced malware behavior and penetration testing. Participants will explore how attackers use these techniques to execute malicious code, bypass security measures, and evade detection.
The course covers a range of key techniques, including Classic Process Injection, Process Hollowing, Unhooking AV Hooks, and Unhooking AV ntdll.dll using PerunsFart. These methods allow attackers to stealthily manipulate and hijack legitimate processes. Students will also learn advanced concepts such as Section Mapping, where memory regions are manipulated for stealthy code execution, and Thread Context manipulation to hijack thread execution.
Additionally, participants will explore Asynchronous Procedure Calls (APCs), which allow attackers to queue code execution within a target process, adding to their toolkit of stealth techniques. Emphasis will be placed on understanding how these techniques are used in real-world attacks and how defenders can detect and mitigate them.
Through hands-on labs and case studies, students will gain practical experience in both the offensive use of these techniques and defensive measures, such as behavioral monitoring and memory analysis. The course will also explore detection strategies using modern tools and methodologies like advanced endpoint detection and response (EDR) systems.
By the end, participants will have a deep understanding of process injection and migration, equipping them to defend against these sophisticated attack methods.
Prerequisites: Basic knowledge of operating systems, programming, and cybersecurity fundamentals.
Who this course is for:
- Red Teamers - Leveling their skills in their world of compromising systems & evading security mechanism
- Blue Teamer - Learn how threat actors work or move in the wild, so they can defend better, protect their systems and educate their fellow workers for better security
- Any-One - Off course, anyone in the Cyber Security field who just wanna learn or know how threat actors act in the wild
User Reviews
Rating
Moreblessing Matake
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 17
- duration 1:34:02
- Release Date 2024/12/25