AKYLADE Certified Cyber Resilience Fundamentals (A/CCRF)
Jason Dion • 1 Million+ Enrollments Worldwide,Dion Training Solutions • ATO for ITIL & PRINCE2,Dion Training Solutions • ATO for ITIL & PRINCE2,Reed Bidgood
7:21:02
Description
Pass the AKYLADE Certified Cyber Resilience Fundamentals (CRF-002) exam on your 1st attempt, includes a practice exam!
What You'll Learn?
- Apply the CSF effectively within their own organizations
- Enhance cyber resilience by managing and mitigating cyber risks
- Communicate the benefits and applications of cyber resilience strategies to stakeholders
- Prepare for and respond to cybersecurity incidents effectively
Who is this for?
What You Need to Know?
More details
DescriptionAKYLADE Certified Cyber Resilience Fundamentals (A/CCRF) (CRF-002) Certification Course
Course Overview
Welcome to the AKYLADE Certified Cyber Resilience Fundamentals (A/CCRF) (CRF-002) course, where you'll master the NIST Cybersecurity Framework (CSF) version 2.0. This course is designed to enhance your understanding and application of the framework within various organizational contexts, focusing on cyber resilience and strategic risk management across multiple sectors.
Domains
The course content is categorized into five distinct domains, emphasizing a structured approach to cyber resilience:
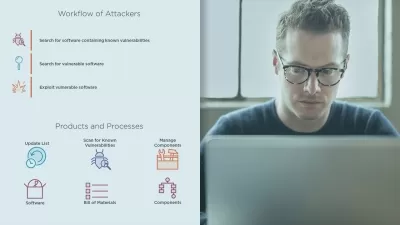
Framework Concepts (25%): Explore the origins, structure, and applicability of the CSF, including its components and key cybersecurity terms.
Framework Core (30%): Delve into the core functions such as Identify, Protect, Detect, Respond, and Recover, integrating 22 categories and 106 subcategories to manage cyber risks.
Implementation Tiers (10%): Understand different maturity levels within an organization’s cybersecurity practices and how to enhance them.
Framework Profiles (15%): Learn to tailor the CSF to specific organizational needs through profiles that adapt to varying risk management strategies.
Risk Management (20%): Gain insights into analyzing and managing cyber risks with practical tools and techniques that support decision-making.
Course Features
Structured Study Guide: Navigate through the CSF with our detailed guide.
Interactive Assessments: Test your knowledge through quizzes and multiple practice exams to reinforce learning.
Learning Outcomes
Participants will finish the course with the ability to apply the CSF effectively within their own organizations, enhance cyber resilience by managing and mitigating cyber risks, communicate the benefits and applications of cyber resilience strategies to stakeholders, and prepare for and respond to cybersecurity incidents effectively.
Intended Learners
This course is targeted at professionals involved in cybersecurity and risk management, including IT managers, security analysts, and compliance officers. It's also ideal for anyone looking to expand their knowledge on implementing and managing the NIST CSF in various sectors such as healthcare, finance, and government.
Requirements
Basic understanding of cybersecurity principles is recommended. Experience in IT or cybersecurity roles is beneficial for contextual application.
Take the Next Step in Cybersecurity Excellence
Enhance your strategic approach to cybersecurity with AKYLADE Certified Cyber Resilience Fundamentals (A/CCRF) (CRF-002). Equip yourself with the skills to advance in the field of cyber resilience.
Enroll Now and Secure Your Future!
What Other Students Are Saying About Our Courses:
This course has really helped me understand how the NIST CSF maps out to the NIST SP 800-53 Rev.5 controls. Very important course to take for those in cyber and information security. (William D., 5 stars)
This course not only explain the NIST CSF, but also gave me many hints on how to implement it in real business situations. (Kenshi K., 5 stars)
Excellent course that helped me gain a better understanding of translating the list of NIST 800 implementations into a practical application I can use for my company and all others we advise on. Thank you! (David S., 5 stars)
Upon completion of this course, you will earn 8 CEUs towards the renewal of your CompTIA A+, Network+, Security+, Linux+, Cloud+, PenTest+, CySA+, or CASP+ certifications.
Who this course is for:
- Professionals involved in cybersecurity and risk management
- IT managers
- Security analysts
- Compliance officers
- Anyone looking to expand their knowledge on implementing and managing the NIST CSF
AKYLADE Certified Cyber Resilience Fundamentals (A/CCRF) (CRF-002) Certification Course
Course Overview
Welcome to the AKYLADE Certified Cyber Resilience Fundamentals (A/CCRF) (CRF-002) course, where you'll master the NIST Cybersecurity Framework (CSF) version 2.0. This course is designed to enhance your understanding and application of the framework within various organizational contexts, focusing on cyber resilience and strategic risk management across multiple sectors.
Domains
The course content is categorized into five distinct domains, emphasizing a structured approach to cyber resilience:
Framework Concepts (25%): Explore the origins, structure, and applicability of the CSF, including its components and key cybersecurity terms.
Framework Core (30%): Delve into the core functions such as Identify, Protect, Detect, Respond, and Recover, integrating 22 categories and 106 subcategories to manage cyber risks.
Implementation Tiers (10%): Understand different maturity levels within an organization’s cybersecurity practices and how to enhance them.
Framework Profiles (15%): Learn to tailor the CSF to specific organizational needs through profiles that adapt to varying risk management strategies.
Risk Management (20%): Gain insights into analyzing and managing cyber risks with practical tools and techniques that support decision-making.
Course Features
Structured Study Guide: Navigate through the CSF with our detailed guide.
Interactive Assessments: Test your knowledge through quizzes and multiple practice exams to reinforce learning.
Learning Outcomes
Participants will finish the course with the ability to apply the CSF effectively within their own organizations, enhance cyber resilience by managing and mitigating cyber risks, communicate the benefits and applications of cyber resilience strategies to stakeholders, and prepare for and respond to cybersecurity incidents effectively.
Intended Learners
This course is targeted at professionals involved in cybersecurity and risk management, including IT managers, security analysts, and compliance officers. It's also ideal for anyone looking to expand their knowledge on implementing and managing the NIST CSF in various sectors such as healthcare, finance, and government.
Requirements
Basic understanding of cybersecurity principles is recommended. Experience in IT or cybersecurity roles is beneficial for contextual application.
Take the Next Step in Cybersecurity Excellence
Enhance your strategic approach to cybersecurity with AKYLADE Certified Cyber Resilience Fundamentals (A/CCRF) (CRF-002). Equip yourself with the skills to advance in the field of cyber resilience.
Enroll Now and Secure Your Future!
What Other Students Are Saying About Our Courses:
This course has really helped me understand how the NIST CSF maps out to the NIST SP 800-53 Rev.5 controls. Very important course to take for those in cyber and information security. (William D., 5 stars)
This course not only explain the NIST CSF, but also gave me many hints on how to implement it in real business situations. (Kenshi K., 5 stars)
Excellent course that helped me gain a better understanding of translating the list of NIST 800 implementations into a practical application I can use for my company and all others we advise on. Thank you! (David S., 5 stars)
Upon completion of this course, you will earn 8 CEUs towards the renewal of your CompTIA A+, Network+, Security+, Linux+, Cloud+, PenTest+, CySA+, or CASP+ certifications.
Who this course is for:
- Professionals involved in cybersecurity and risk management
- IT managers
- Security analysts
- Compliance officers
- Anyone looking to expand their knowledge on implementing and managing the NIST CSF
User Reviews
Rating
Jason Dion • 1 Million+ Enrollments Worldwide
Instructor's CoursesDion Training Solutions • ATO for ITIL & PRINCE2
Instructor's CoursesDion Training Solutions • ATO for ITIL & PRINCE2
Instructor's CoursesReed Bidgood
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 88
- duration 7:21:02
- Release Date 2024/08/11