Adversarial Machine Learning with CSV and Image Data
1:38:31
Description
Mastering Adversarial Machine Learning: Insights into Attack Techniques, Defense Strategies, and Ethical Considerations
What You'll Learn?
- Explain foundational adversarial ML concepts, including AI security challenges and historical evolution.
- Analyze different adversarial attack types and assess their impact on machine learning models.
- Develop and apply defensive techniques for CSV and image-based ML models to mitigate risks.
- Use generative adversarial networks (GANs) to craft adversarial examples and test model robustness.
- Explore ethical considerations in adversarial ML.
- Investigate emerging trends in adversarial machine learning, including quantum computing, edge computing, zero-shot learning, and reinforcement learning
Who is this for?
What You Need to Know?
More details
DescriptionThis comprehensive course on Adversarial Machine Learning (AML) offers a deep dive into the complex world of AI security, teaching you the sophisticated techniques used for both attacking and defending machine learning models. Throughout this course, you will explore the critical aspects of adversarial attacks, including their types, evolution, and the methodologies used to craft them, with a special focus on CSV and image data.
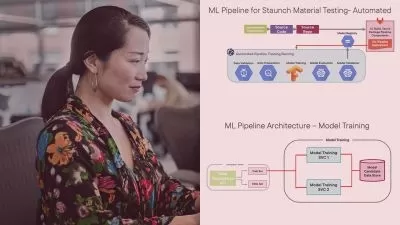
Starting with an introduction to the fundamental challenges in AI security, the course guides you through the various phases of setting up a robust adversarial testing environment. You will gain hands-on experience in simulating adversarial attacks on models trained with different data types and learn how to implement effective defenses to protect these models.
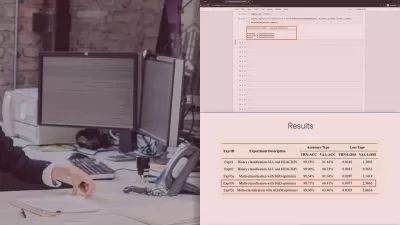
The curriculum includes detailed practical sessions where you will craft evasion attacks, analyze the impact of these attacks on model performance, and apply cutting-edge defense mechanisms. The course also covers advanced topics such as the transferability of adversarial examples and the use of Generative Adversarial Networks (GANs) in AML practices.
By the end of this course, you will not only understand the technical aspects of AML but also appreciate the ethical considerations in deploying these strategies. This course is ideal for cybersecurity professionals, data scientists, AI researchers, and anyone interested in enhancing the security and integrity of machine learning systems.
Who this course is for:
- This Adversarial Machine Learning course is ideal for AI professionals, cybersecurity experts, data scientists, graduate/post graduate/doctoral/post-doctoral students in related fields, and tech enthusiasts with a foundation in machine learning and programming, who are interested in exploring the security challenges of AI systems.
This comprehensive course on Adversarial Machine Learning (AML) offers a deep dive into the complex world of AI security, teaching you the sophisticated techniques used for both attacking and defending machine learning models. Throughout this course, you will explore the critical aspects of adversarial attacks, including their types, evolution, and the methodologies used to craft them, with a special focus on CSV and image data.
Starting with an introduction to the fundamental challenges in AI security, the course guides you through the various phases of setting up a robust adversarial testing environment. You will gain hands-on experience in simulating adversarial attacks on models trained with different data types and learn how to implement effective defenses to protect these models.
The curriculum includes detailed practical sessions where you will craft evasion attacks, analyze the impact of these attacks on model performance, and apply cutting-edge defense mechanisms. The course also covers advanced topics such as the transferability of adversarial examples and the use of Generative Adversarial Networks (GANs) in AML practices.
By the end of this course, you will not only understand the technical aspects of AML but also appreciate the ethical considerations in deploying these strategies. This course is ideal for cybersecurity professionals, data scientists, AI researchers, and anyone interested in enhancing the security and integrity of machine learning systems.
Who this course is for:
- This Adversarial Machine Learning course is ideal for AI professionals, cybersecurity experts, data scientists, graduate/post graduate/doctoral/post-doctoral students in related fields, and tech enthusiasts with a foundation in machine learning and programming, who are interested in exploring the security challenges of AI systems.
User Reviews
Rating

Udemy
View courses Udemy- language english
- Training sessions 20
- duration 1:38:31
- Release Date 2025/03/08